| 文章转载于雾晓安全
0x00 EDRHunt前言
由于Windows市场上提供了大量端点检测和响应系统(EDR)和防病毒解决方案,因此在红队操作期间,迫切需要在目标端点上对这些已安装的解决方案进行指纹识别。事实证明,这些信息对于定制自定义漏洞利用和攻击技术以成功渗透和对目标进行操作至关重要。EDRHunt是一个实用程序,可通过查询服务、驱动程序、运行进程和注册表项来扫描和识别Windows端点上已安装的EDR和AV。
0x01 EDRHunt介绍
EDRHunt扫描Windows服务、驱动程序、进程、注册表以查找已安装的EDR(端点检测和响应)
0x02 EDRHunt检测
目前可用的 EDR 检测
Windows Defender 卡巴斯基安全 赛门铁克安全 Crowdstrike Security 迈克菲安全 Cylance安全 Carbon Black SentinelOne 火眼
0x03 EDRHunt安装
二进制
从发布部分下载最新版本,发行版是为windows/amd64构建。
GO
需要在系统上安装Go。在Go1.17+上测试
go install github.com/FourCoreLabs/EDRHunt/cmd/EDRHunt@master复制
0x04 EDRHunt使用
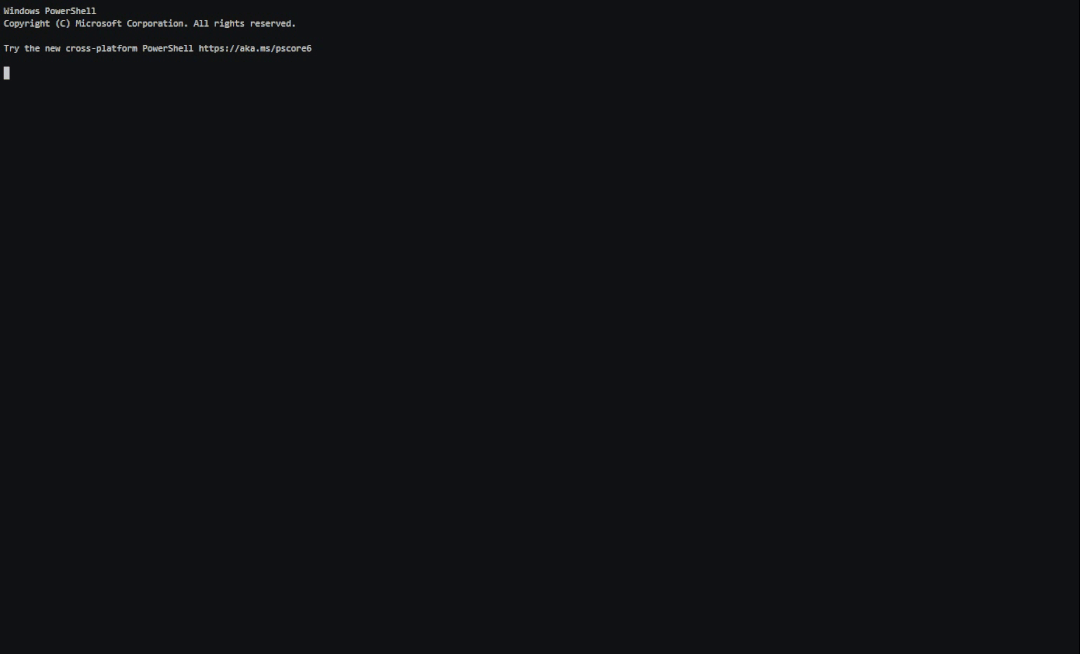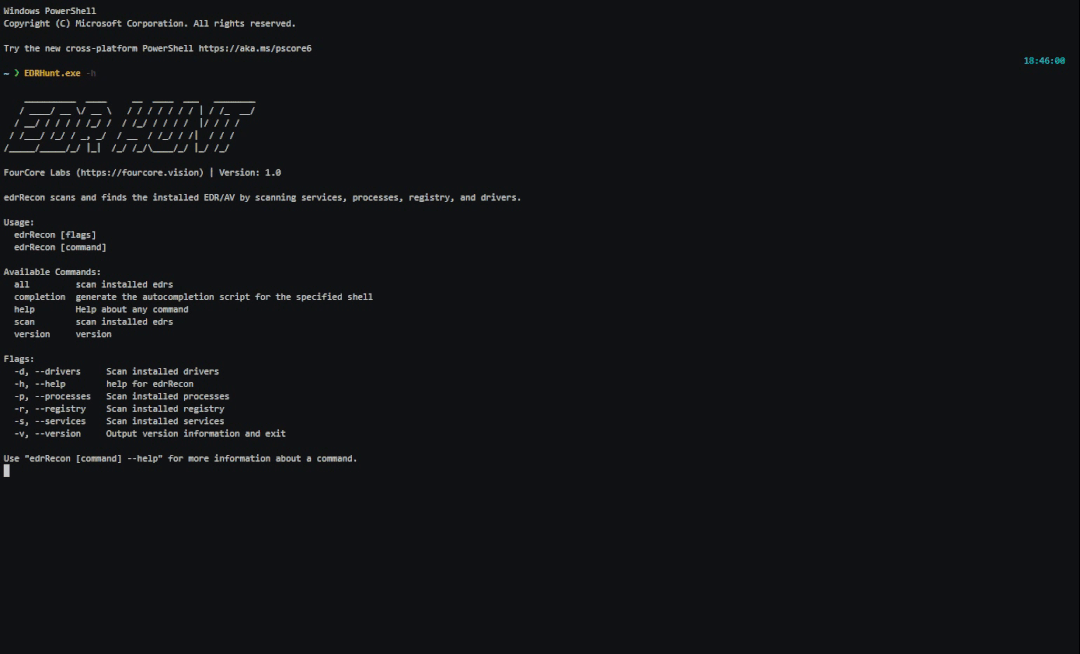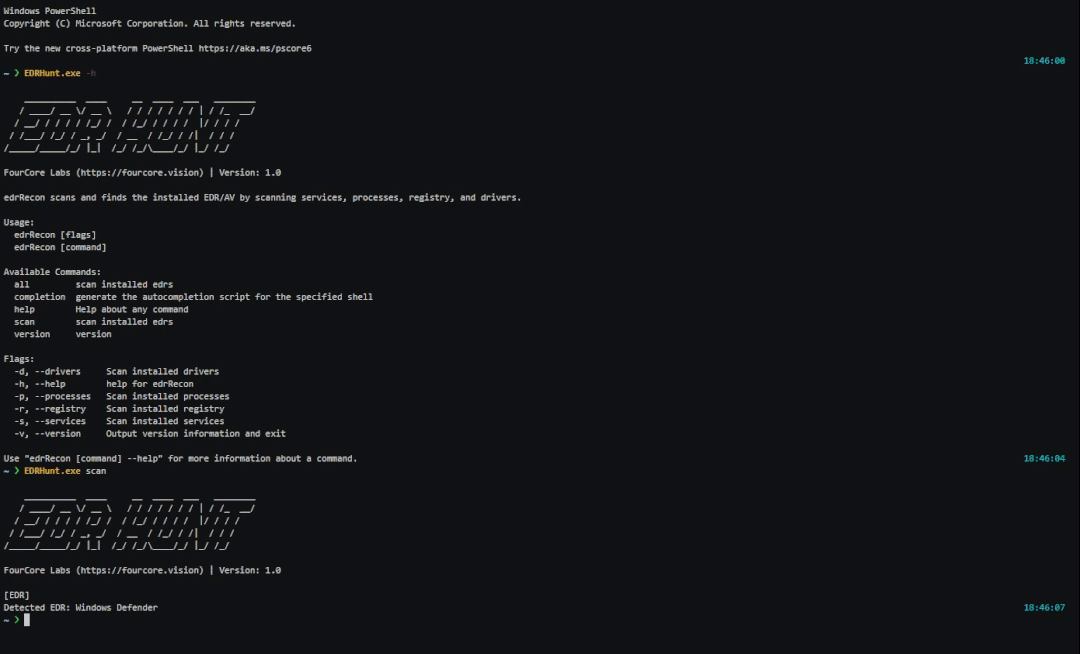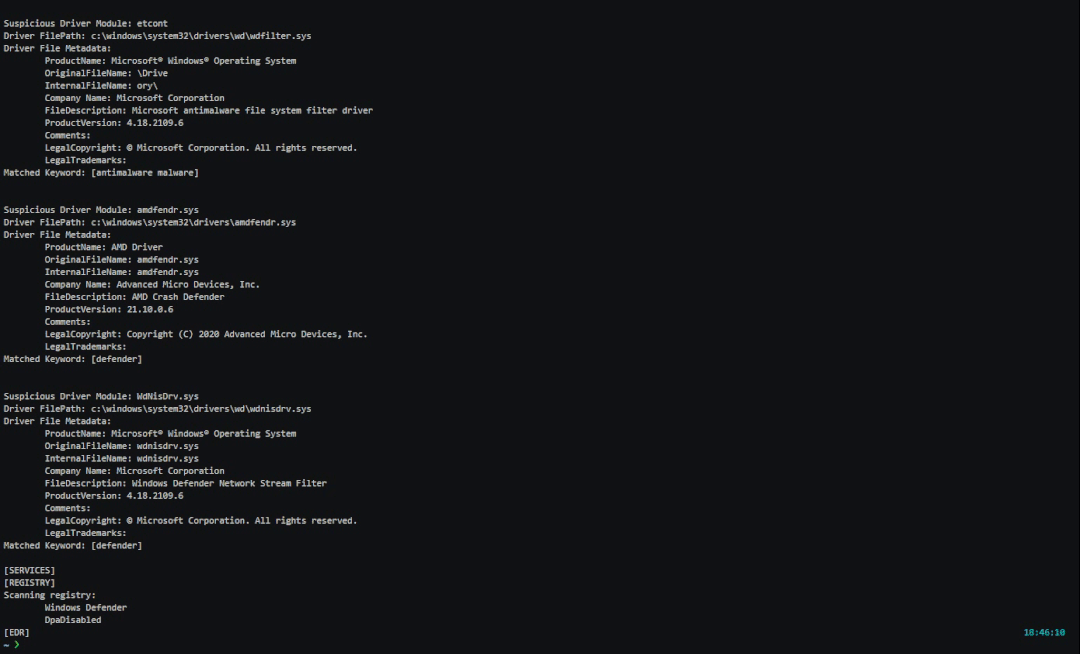
查找已安装的EDR
$ .\EDRHunt.exe scan
[EDR]
Detected EDR: Windows Defender
Detected EDR: Kaspersky Security复制
扫描一切
$ .\EDRHunt.exe all
Running in user mode, escalate to admin for more details.
Scanning processes, services, drivers, and registry...
[PROCESSES]
Suspicious Process Name: MsMpEng.exe
Description: MsMpEng.exe
Caption: MsMpEng.exe
Binary:
ProcessID: 6764
Parent Process: 1148
Process CmdLine :
File Metadata:
Matched Keyword: [msmpeng]
Suspicious Process Name: NisSrv.exe
Description: NisSrv.exe
Caption: NisSrv.exe
Binary:
ProcessID: 9840
Parent Process: 1148
Process CmdLine :
File Metadata:
Matched Keyword: [nissrv]
...复制
查找匹配EDR关键字的驱动程序
更进一步,我们还可以扫描已安装的驱动程序及其驱动程序元数据,以识别由防病毒解决方案安装的驱动程序以执行./EDRHunt.exe -d此外,我们还可以识别各种重要的关键字,包括defender和antimalware,这表示系统上正在运行WindowsDefender。
$ .\EDRHunt.exe -p
__________ ____ __ ____ ___ ________
/ ____/ __ \/ __ \ / / / / / / / | / /_ __/
/ __/ / / / / /_/ / / /_/ / / / / |/ / / /
/ /___/ /_/ / _, _/ / __ / /_/ / /| / / /
/_____/_____/_/ |_| /_/ /_/\____/_/ |_/ /_/
FourCore Labs (https://fourcore.vision) | Version: 1.0
Running in user mode, escalate to admin for more details.
[PROCESSES]
Suspicious Process Name: MsMpEng.exe
...
Matched Keyword: [msmpeng]
Suspicious Process Name: NisSrv.exe
...
Matched Keyword: [nissrv]
Suspicious Process Name: SecurityHealthService.exe
Description: SecurityHealthService.exe
...
Matched Keyword: [securityhealthservice]
...复制
查找匹配EDR关键字的服务
可以识别重要的关键字,包括securityhealthservice, m
spmeng,这意味着系统上正在运行Windows Defender服务。
$ .\EDRHunt.exe -s
__________ ____ __ ____ ___ ________
/ ____/ __ \/ __ \ / / / / / / / | / /_ __/
/ __/ / / / / /_/ / / /_/ / / / / |/ / / /
/ /___/ /_/ / _, _/ / __ / /_/ / /| / / /
/_____/_____/_/ |_| /_/ /_/\____/_/ |_/ /_/
FourCore Labs (https://fourcore.vision) | Version: 1.0
Running in user mode, escalate to admin for more details.
[SERVICES]
...
Suspicious Service Name: SecurityHealthService
Display Name: Windows Security Service
...
Matched Keyword: [securityhealthservice]
Suspicious Service Name: Sense
Display Name: Windows Defender Advanced Threat Protection Service
...
Matched Keyword: [defender threat]
Suspicious Service Name: WdNisSvc
Display Name: Microsoft Defender Antivirus Network Inspection Service
...
Matched Keyword: [antivirus defender nissrv]
Suspicious Service Name: WinDefend
Display Name: Microsoft Defender Antivirus Service
...
Matched Keyword: [antimalware antivirus defender malware msmpeng]
...复制
查找匹配EDR关键字的驱动程序
更进一步,我们还可以扫描已安装的驱动程序及其驱动程序元数据,以识别由防病毒解决方案安装的驱动程序以执行./EDRHunt.exe -d此外,我们还可以识别各种重要的关键字,包括defender和antimalware,这表示系统上正在运行Windows Defender。
$ .\EDRHunt.exe -d
__________ ____ __ ____ ___ ________
/ ____/ __ \/ __ \ / / / / / / / | / /_ __/
/ __/ / / / / /_/ / / /_/ / / / / |/ / / /
/ /___/ /_/ / _, _/ / __ / /_/ / /| / / /
/_____/_____/_/ |_| /_/ /_/\____/_/ |_/ /_/
FourCore Labs (https://fourcore.vision) | Version: 1.0
Running in user mode, escalate to admin for more details.
[DRIVERS]
Suspicious Driver Module: WdFilter.sys
Driver FilePath: c:\windows\system32\drivers\wd\wdfilter.sys
Driver File Metadata:
ProductName: Microsoft® Windows® Operating System
OriginalFileName: WdFilter.sys
InternalFileName: WdFilter
Company Name: Microsoft Corporation
FileDescription: Microsoft antimalware file system filter driver
ProductVersion: 4.18.2109.6
Comments:
LegalCopyright: © Microsoft Corporation. All rights reserved.
LegalTrademarks:
Matched Keyword: [antimalware malware]
Suspicious Driver Module: hvsifltr.sys
Driver FilePath: c:\windows\system32\drivers\hvsifltr.sys
Driver File Metadata:
ProductName: Microsoft® Windows® Operating System
OriginalFileName: hvsifltr.sys.mui
InternalFileName: hvsifltr.sys
Company Name: Microsoft Corporation
FileDescription: Microsoft Defender Application Guard Filter Driver
ProductVersion: 10.0.19041.1
Comments:
LegalCopyright: © Microsoft Corporation. All rights reserved.
LegalTrademarks:
Matched Keyword: [defender]复制
查找与EDR关键字匹配的注册表项
$ .\EDRHunt.exe -r复制
0x05 获取
https://github.com/FourCoreLabs/EDRHunt
更多技术文章请关注公众号:






