点击上方"walkingcloud"关注,并选择"星标"公众号

Shadowsocks 是一个轻量级的 SOCKS5 网络代理工具,主要用于绕过网络censorship并访问被阻止的某些网站和网络协议
与其他代理软件不同,Shadowsocks 流量被设计为既与其他流量无法区分到第三方监控工具,也可以伪装成正常的直连。通过 Shadowsocks 的数据经过加密以提高安全性和隐私性。
一、rpm包方式安装并部署shadowsocks
1、配置EPEL源
curl -o /etc/yum.repos.d/epel.repo http://mirrors.aliyun.com/repo/epel-7.repo
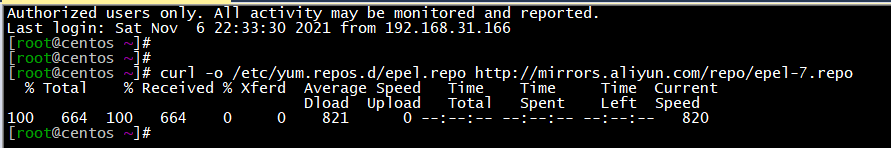
(图片可点击放大查看)
2、上传shadowsocks-libev的rpm并安装
yum localinstall shadowsocks-libev-3.2.0-2.el7.x86_64.rpm
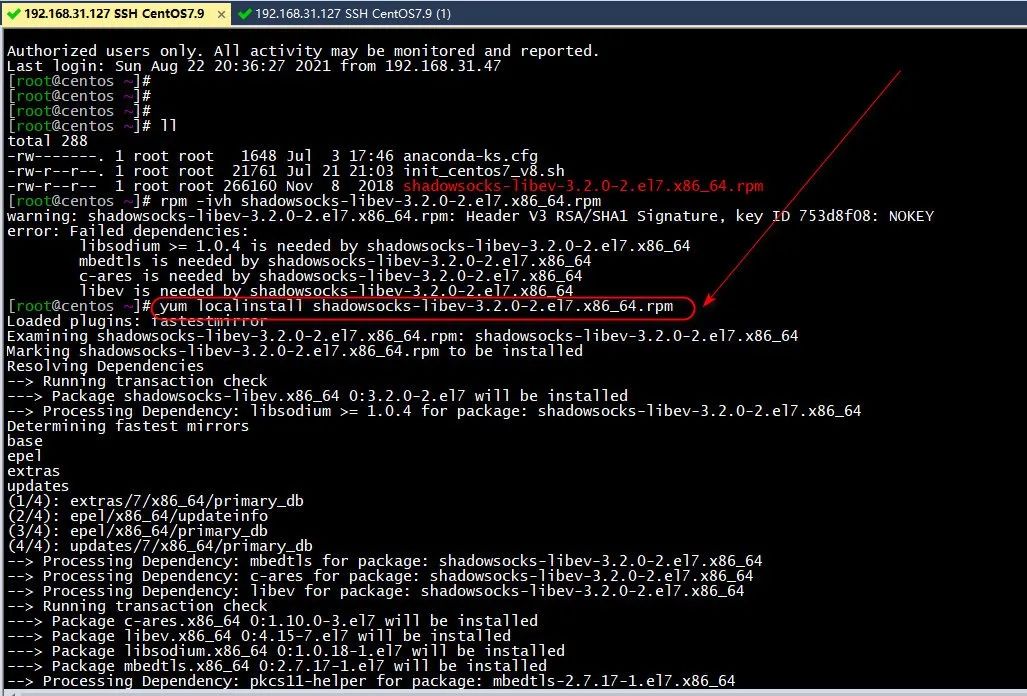
(图片可点击放大查看)
3、配置sysctl内核参数
vi /etc/sysctl.d/shadowsocks.conf
添加如下参数
# max open files
fs.file-max = 51200
# max read buffer
net.core.rmem_max = 67108864
# max write buffer
net.core.wmem_max = 67108864
# default read buffer
net.core.rmem_default = 65536
# default write buffer
net.core.wmem_default = 65536
# max processor input queue
net.core.netdev_max_backlog = 4096
# max backlog
net.core.somaxconn = 4096
# resist SYN flood attacks
net.ipv4.tcp_syncookies = 1
# reuse timewait sockets when safe
net.ipv4.tcp_tw_reuse = 1
# turn off fast timewait sockets recycling
net.ipv4.tcp_tw_recycle = 0
# short FIN timeout
net.ipv4.tcp_fin_timeout = 30
# short keepalive time
net.ipv4.tcp_keepalive_time = 1200
# outbound port range
net.ipv4.ip_local_port_range = 10000 65000
# max SYN backlog
net.ipv4.tcp_max_syn_backlog = 4096
# max timewait sockets held by system simultaneously
net.ipv4.tcp_max_tw_buckets = 5000
# turn on TCP Fast Open on both client and server side
net.ipv4.tcp_fastopen = 3
# TCP receive buffer
net.ipv4.tcp_rmem = 4096 87380 67108864
# TCP write buffer
net.ipv4.tcp_wmem = 4096 65536 67108864
# turn on path MTU discovery
net.ipv4.tcp_mtu_probing = 1
# for high-latency network
net.ipv4.tcp_congestion_control = hybla
# for low-latency network, use cubic instead
net.ipv4.tcp_congestion_control = cubic
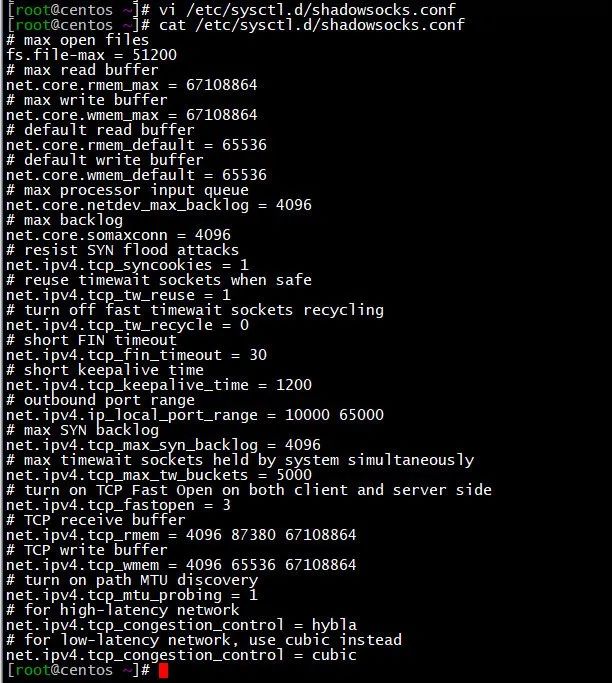
(图片可点击放大查看)
使参数生效
sysctl --system
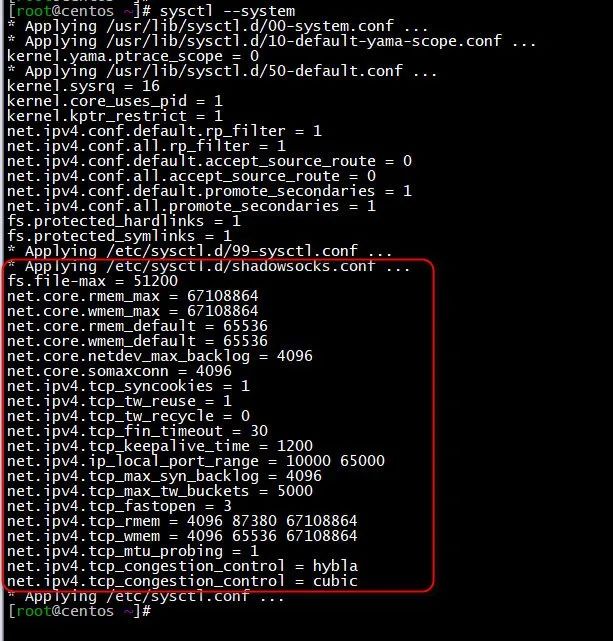
(图片可点击放大查看)
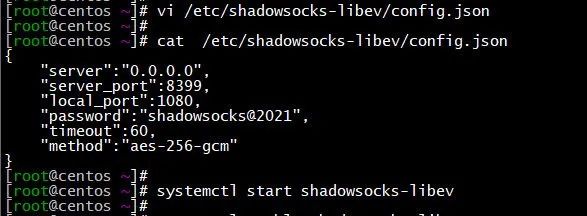
4、修改config.json配置文件
vi /etc/shadowsocks-libev/config.json
修改为如下
{
"server":"0.0.0.0",
"server_port":8399,
"local_port":1080,
"password":"shadowsocks@2021",
"timeout":60,
"method":"aes-256-gcm"
}
(图片可点击放大查看)
"server":选填,默认 "0.0.0.0"。配置客户端时填入服务器的实际 IP。"0.0.0.0" 表明服务端接受来自任何网络接口的连接
"server_port":必填。需要在客户端配置时填入相同的值,建议修改默认的8388为其他端口
"password":必填。需要在客户端配置时填入相同的值。连接服务端所需的密码,建议替换为复杂密码,避免被攻击者暴力破解
"method":选填,服务端所用的加密方法。需要在客户端配置时填入相同的值。可以使用"aes-256-gcm" 具有足够安全性,且被各服务端及客户端广泛支持
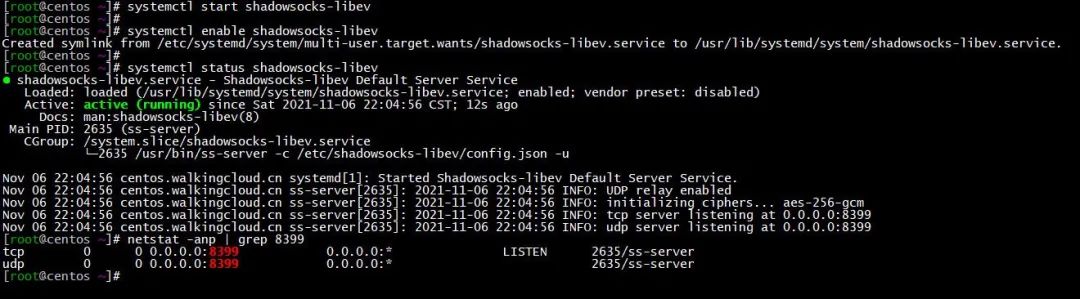
5、启动shadowsocks-libev服务
systemctl start shadowsocks-libev
systemctl enable shadowsocks-libev
systemctl status shadowsocks-libev
(图片可点击放大查看)
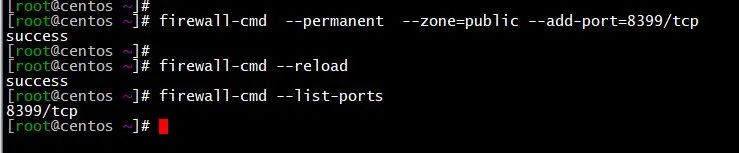
并放通端口
firewall-cmd --permanent --zone=public --add-port=8399/tcp
firewall-cmd --reload
firewall-cmd --list-ports
netstat -anp | grep 8399
(图片可点击放大查看)
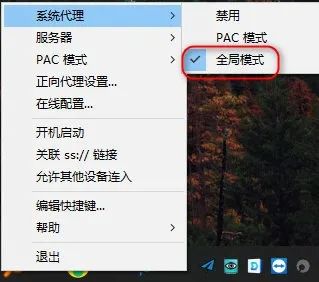
6、windows客户端配置并验证代理上网效果
下载地址https://github.com/shadowsocks/shadowsocks-windows/releases
设置为全局模式,并添加服务器配置
(图片可点击放大查看)
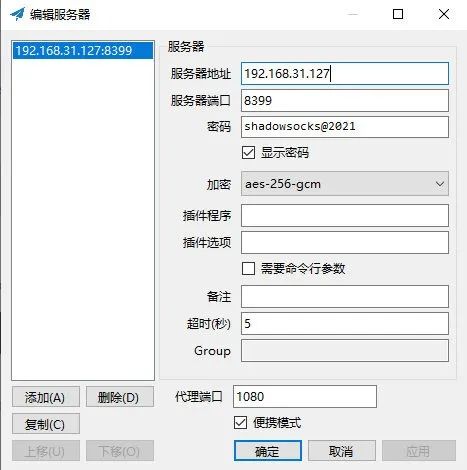
(图片可点击放大查看)
验证效果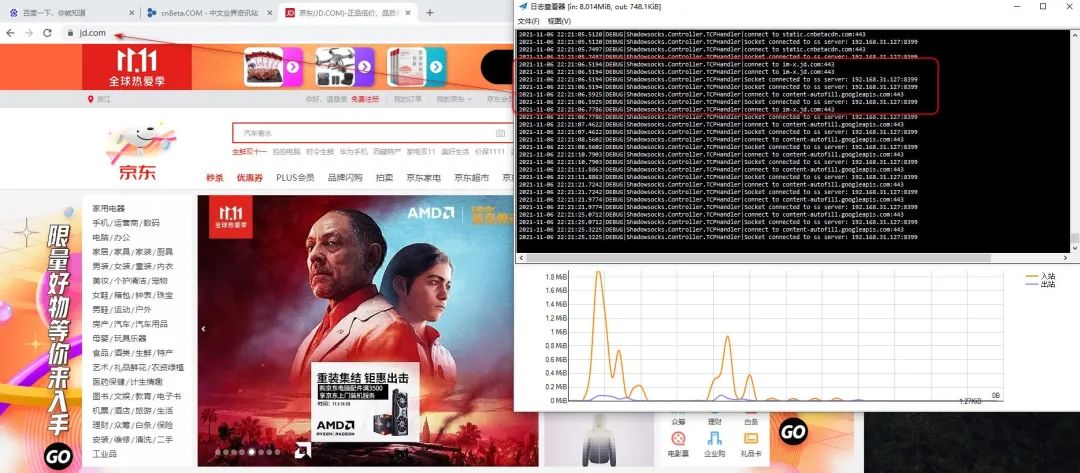
(图片可点击放大查看)
7、Linux下使用代理
通过上面windows10主机192.168.31.166作为局域网代理进行上网
需要提前设置代理端口:例如11080

(图片可点击放大查看)
防火墙开放11080端口

(图片可点击放大查看)
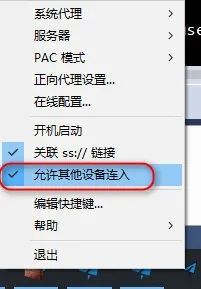
并允许其它设备接入
Linux服务器本身无法上网(通过修改原默认网关192.168.31.1为不通的内网地址192.168.31.254进行模拟)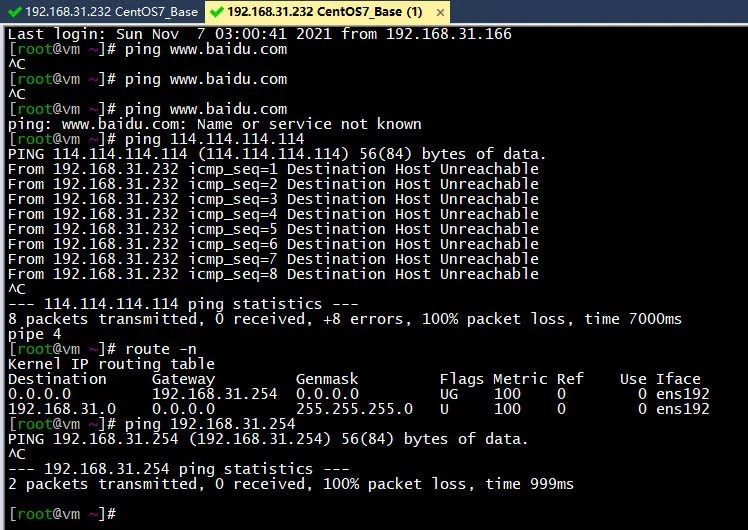
(图片可点击放大查看)
vi /etc/profile
添加如下行
export https_proxy=http://192.168.31.166:11080
export http_proxy=http://192.168.31.166:11080
#使生效
source /etc/profile
验证
curl -k https://www.baidu.com
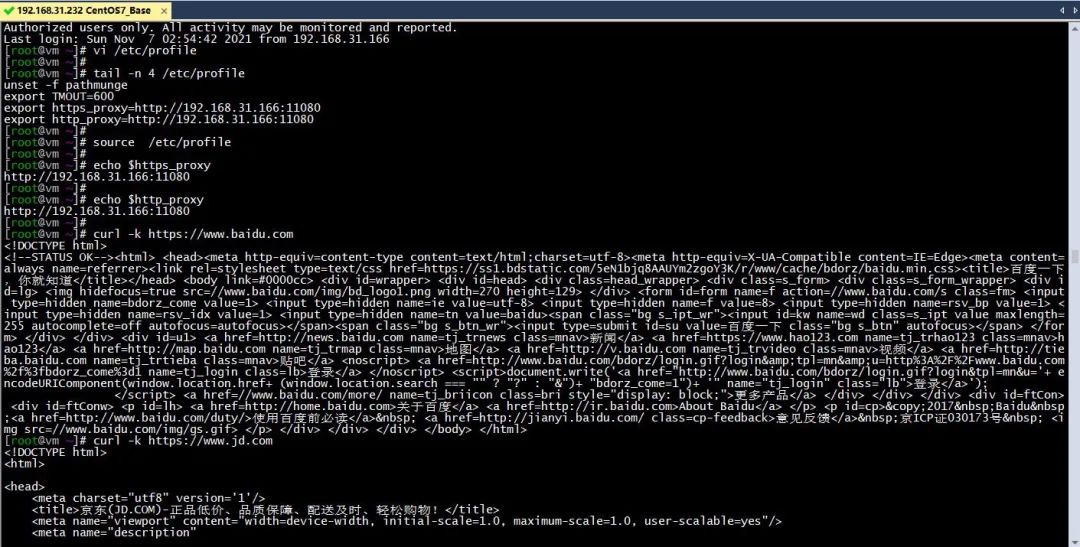
(图片可点击放大查看)
二、源码编译安装并配置shadowsocks-libev
当然你可以也使用源码编译的方式安装 具体方法如下(就不截图展示了)
1、 CentOS7下安装依赖包
yum install -y gcc gettext autoconf libtool automake make pcre-devel asciidoc xmlto udns-devel \
libev-devel libsodium-devel mbedtls-devel git m2crypto c-ares-devel
2、编译方装
cd /opt
git clone https://github.com/shadowsocks/shadowsocks-libev.git
cd shadowsocks-libev
git submodule update --init --recursive
./autogen.sh
./configure
make && make install
3、创建shadowsocks用户及shadowsocks配置文件
adduser --system --no-create-home -s /bin/false shadowsocks
mkdir -m 755 /etc/shadowsocks
vi /etc/shadowsocks/shadowsocks.json
{
"server":"IP_address",
"server_port":8388,
"password":"password",
"timeout":300,
"method":"aes-256-gcm",
"fast_open": true
}
4、配置sysctl内核参数
vi /etc/sysctl.d/shadowsocks.conf
添加参数(见上面的步骤)
sysctl --system
5、创建服务shadowsocks的systemd服务
vi /etc/systemd/system/shadowsocks.service
添加如下行
[Unit]
Description=Shadowsocks proxy server
[Service]
User=root
Group=root
Type=simple
ExecStart=/usr/local/bin/ss-server -c /etc/shadowsocks/shadowsocks.json -a shadowsocks -v start
ExecStop=/usr/local/bin/ss-server -c /etc/shadowsocks/shadowsocks.json -a shadowsocks -v stop
[Install]
WantedBy=multi-user.target
systemctl daemon-reload
systemctl enable shadowsocks
systemctl start shadowsocks
配置方法与rpm安装的方式大同小异, 这里就不再验证测试效果






