适用范围
Linux平台下为解决安全漏洞CVE-2016-2183 进行升级OpenSSL版本。
问题描述
SSL/TLS协议信息泄露漏洞(CVE-2016-2183)
TLS是安全传输层协议,用于在两个通信应用程序之间提供保密性和数据完整性。
TLS, SSH, IPSec协商及其他产品中使用的DES及Triple DES密码存在大约四十亿块的生日界,这可使远程攻击者通过Sweet32攻击,获取纯文本数据。
方案概述
漏洞(CVE-2016-2183) 是属于通过安全协议访问服务时存在用户名密码这些信息泄露的可能性,10005端口为 ReplicationManager的 API访问端口 ,也就是说 ReplicationManager 可以通过10005端口 进行对Replication Manager的web 页面访问,也就是说如果在linux环境通过https协议来进行对Replication Manager管理页面的访问,就可能会有此风险。在OS层面走这种SSL/TLS是通过 openssl这个软件来提供这个功能的,我们在 openssl官方也找到该漏洞的说明:
SWEET32 Mitigation (CVE-2016-2183)
==================================
Severity: Low
SWEET32 (https://sweet32.info) is an attack on older block cipher algorithms
that use a block size of 64 bits. In mitigation for the SWEET32 attack DES based
ciphersuites have been moved from the HIGH cipherstring group to MEDIUM in
OpenSSL 1.0.1 and OpenSSL 1.0.2. OpenSSL 1.1.0 since release has had these
ciphersuites disabled by default.
OpenSSL 1.0.2 users should upgrade to 1.0.2i
OpenSSL 1.0.1 users should upgrade to 1.0.1u
This issue was reported to OpenSSL on 16th August 2016 by Karthikeyan
Bhargavan and Gaetan Leurent (INRIA). The fix was developed by Rich Salz of the
OpenSSL development team.
说明:该漏洞 openssl官网给出的解决方案为 升级 Openssl的版本,在高版本中解决了该问题。为此我还查询了一下当前主机的Openssl版本,确实为低版本:1.0.2k
# openssl version
OpenSSL 1.0.2k-fips 26 Jan 2017
实施步骤
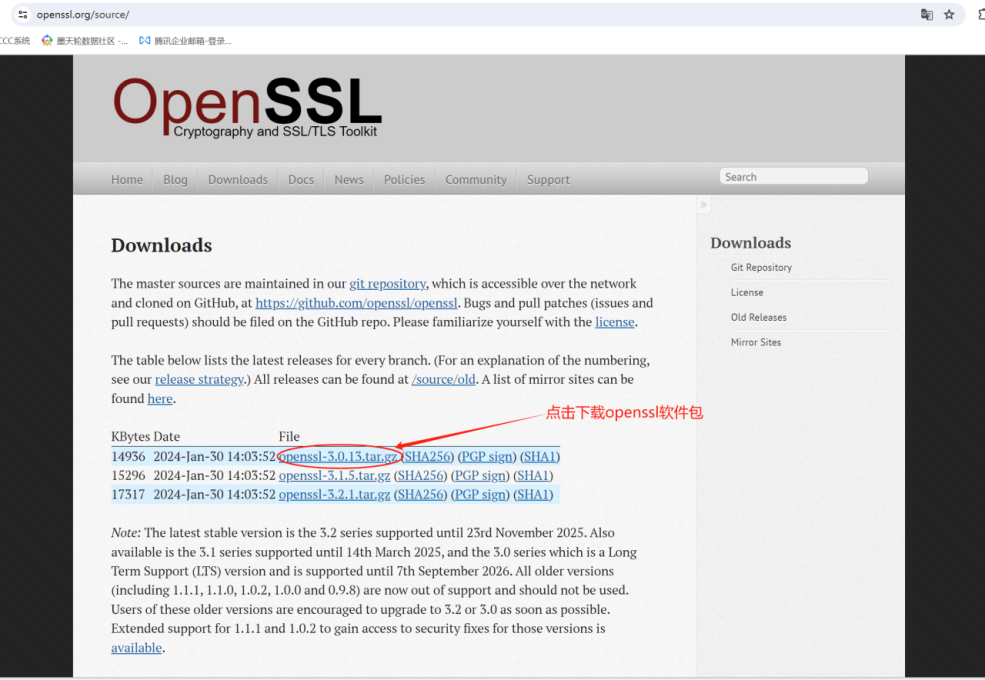
1. 下载openssl软件包
通过访问openssl官方网站https://www.openssl.org/source/ 进行下载:
2. 上传软件并解压
上传至服务器,我这里是直接将软件包上传至服务器/backup目录下
[root@localhost ~]# cd /backup
[root@localhost backup]# ls -lhrt
total 15M
drwxr-xr-x 2 oracle oinstall 87 Feb 22 17:51 dmpdata
-rw-r--r-- 1 root root 15M Mar 20 16:11 openssl-3.0.13.tar.gz
##解压软件
[root@localhost backup]# tar xvf openssl-3.0.13.tar.gz
[root@localhost backup]# cd openssl-3.0.13
3. 升级前的版本确认
[root@localhost ~]# openssl version
OpenSSL 1.0.2k-fips 26 Jan 2017
[root@localhost ~]#
[root@localhost ~]# openssl version -a
OpenSSL 1.0.2k-fips 26 Jan 2017
built on: reproducible build, date unspecified
platform: linux-x86_64
options: bn(64,64) md2(int) rc4(16x,int) des(idx,cisc,16,int) idea(int) blowfish(idx)
compiler: gcc -I. -I.. -I../include -fPIC -DOPENSSL_PIC -DZLIB -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -DKRB5_MIT
-m64 -DL_ENDIAN -Wall -O2 -g -pipe -Wall -Wp,-D_FORTIFY_SOURCE=2 -fexceptions -fstack-protector-strong --param=ssp-buffer-size=4 -gre
cord-gcc-switches -m64 -mtune=generic -Wa,--noexecstack -DPURIFY -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -
DOPENSSL_BN_ASM_GF2m -DRC4_ASM -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DMD5_ASM -DAES_ASM -DVPAES_ASM -DBSAES_ASM -DWHIRLPOOL_ASM -DGHA
SH_ASM -DECP_NISTZ256_ASM
OPENSSLDIR: "/etc/pki/tls"
engines: dynamic
[root@localhost ~]# which openssl
/usr/bin/openssl
[root@localhost ~]# rpm -qa|grep openssl
openssl-libs-1.0.2k-21.el7_9.x86_64
openssl-devel-1.0.2k-21.el7_9.x86_64
xmlsec1-openssl-1.2.20-7.el7_4.x86_64
openssl-1.0.2k-21.el7_9.x86_64
[root@localhost ~]#
说明:升级前openssl的版本为1.0.2k
4. 编译安装新版本
root@localhost backup]# mkdir -p /usr/local/openssl
##生成 Makefile,为编译做准备
[root@localhostbackup]# cd /backup/openssl-3.0.13
[root@localhostbackup]# ./config --prefix=/usr/local/openssl/
Configuring OpenSSL version 3.0.13 for target linux-x86_64
Using os-specific seed configuration
Created configdata.pm
Running configdata.pm
Created Makefile.in
Created Makefile
Created include/openssl/configuration.h
**********************************************************************
*** ***
*** OpenSSL has been successfully configured ***
*** ***
*** If you encounter a problem while building, please open an ***
*** issue on GitHub <https://github.com/openssl/openssl/issues> ***
*** and include the output from the following command: ***
*** ***
*** perl configdata.pm --dump ***
*** ***
*** (If you are new to OpenSSL, you might want to consult the ***
*** 'Troubleshooting' section in the INSTALL.md file first) ***
*** ***
**********************************************************************
[root@localhostbackup]# make
[root@localhost backup]# make install
5. 备份老版本openssl相关数据
[root@localhost openssl-3.0.1]# mv /usr/bin/openssl /usr/bin/openssl.old
[root@localhost openssl-3.0.1]# mv /usr/include/openssl/ /usr/include/openssl.old
6. 配置软链接
[root@localhost openssl-3.0.1]# ln -s /usr/local/openssl/bin/openssl /usr/bin/openssl
[root@localhost openssl-3.0.1]# ln -s /usr/local/openssl/include/openssl /usr/include/openssl
[root@localhost openssl-3.0.1]# echo "/usr/local/openssl/lib64/" >> /etc/ld.so.conf
7. 生效和查看版本
[root@localhost openssl-3.0.1]# cd /backup/openssl-3.0.13
[root@localhost openssl-3.0.1]# ldconfig
#ldconfig是一个动态链接库管理命令,其目的为了让动态链接库为系统所共享
#查看升级后的新版本
[root@localhost openssl-3.0.13]# openssl version
OpenSSL 3.0.13 30 Jan 2024 (Library: OpenSSL 3.0.13 30 Jan 2024)
[root@localhost openssl-3.0.13]#
[root@localhost openssl-3.0.13]#
[root@localhost openssl-3.0.13]# openssl version -a
OpenSSL 3.0.13 30 Jan 2024 (Library: OpenSSL 3.0.13 30 Jan 2024)
built on: Wed Mar 20 09:01:54 2024 UTC
platform: linux-x86_64
options: bn(64,64)
compiler: gcc -fPIC -pthread -m64 -Wa,--noexecstack -Wall -O3 -DOPENSSL_USE_NODELETE -DL_ENDIAN -DOPENSSL_PIC -DOPENSSL_BUILDING_OPEN
SSL -DNDEBUG
OPENSSLDIR: "/usr/local/openssl/ssl"
ENGINESDIR: "/usr/local/openssl//lib64/engines-3"
MODULESDIR: "/usr/local/openssl//lib64/ossl-modules"
Seeding source: os-specific
CPUINFO: OPENSSL_ia32cap=0x1fbee3ffffebffff:0x0
说明:至此openssl软件包升级成功!
8. 可能遇到的错误
/**** 编译时如果遇到下面错误,需要安装对应的工具包perl-ExtUtils-CBuilder 和 perl-ExtUtils-MakeMaker
##生成 Makefile,为编译做准备
[root@localhost openssl-3.0.1]#./config --prefix=/usr/local/ssl/
Can't locate IPC/Cmd.pm in @INC (@INC contains: /opt/openssl-3.0.1/util/perl /usr/local/lib64/perl5 /usr/local/share/perl5 /usr/lib64/perl5/vendor_perl /usr/share/perl5/vendor_perl /usr/lib64/perl5 /usr/share/perl5 . /opt/openssl-3.0.1/external/perl/Text-Template-1.56/lib) at /opt/openssl-3.0.1/util/perl/OpenSSL/config.pm line 18.
BEGIN failed--compilation aborted at /opt/openssl-3.0.1/util/perl/OpenSSL/config.pm line 18.
Compilation failed in require at /opt/openssl-3.0.1/Configure line 23.
BEGIN failed--compilation aborted at /opt/openssl-3.0.1/Configure line 23.
解决办法:
安装所关联的软件包和编译工具包
[root@localhost openssl-3.0.1]#yum install perl-ExtUtils-CBuilder perl-ExtUtils-MakeMaker
附录:关于ssh的算法
ssh本身提供了一些加密算法,默认ssh是使用3DES加密算法,但是该DES算法会被漏洞利用,所以想在ssh移除某种算法,可以在配置文件中删除即可。
# sshd -T |grep ciphers
ciphers chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,blowfish-cbc,cast128-cbc,3des-cbc
可以在/etc/ssh/ssh_config or ~/.ssh/config文件中看到
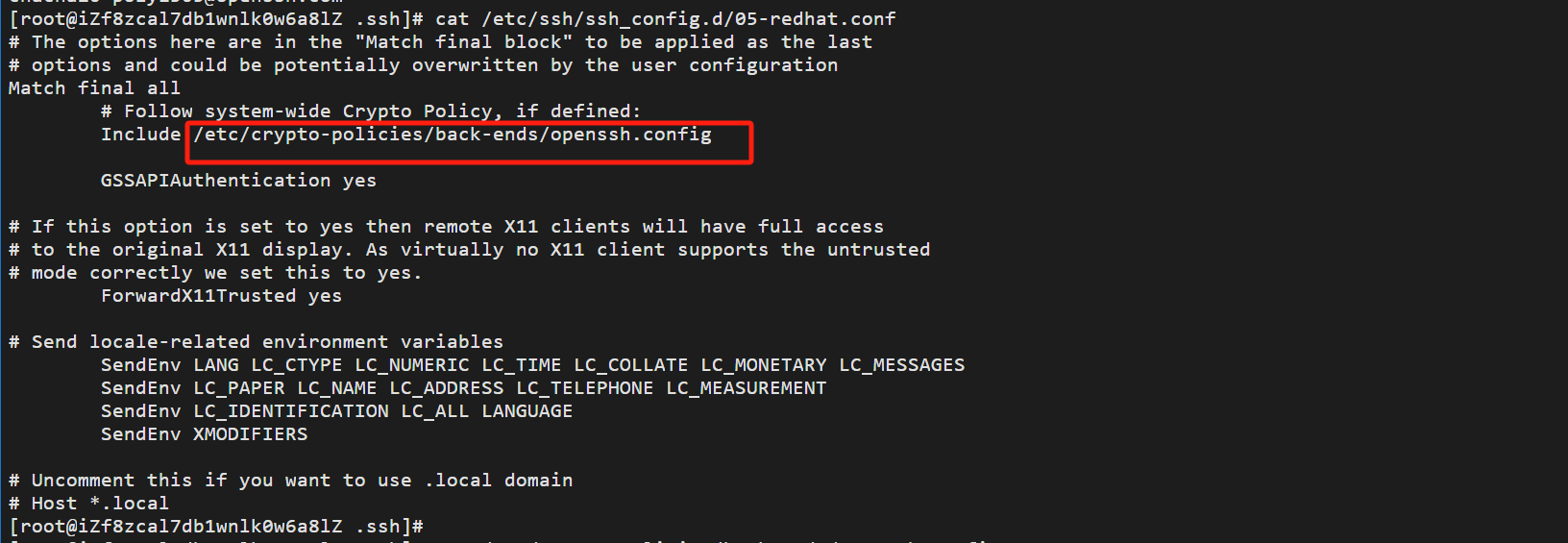
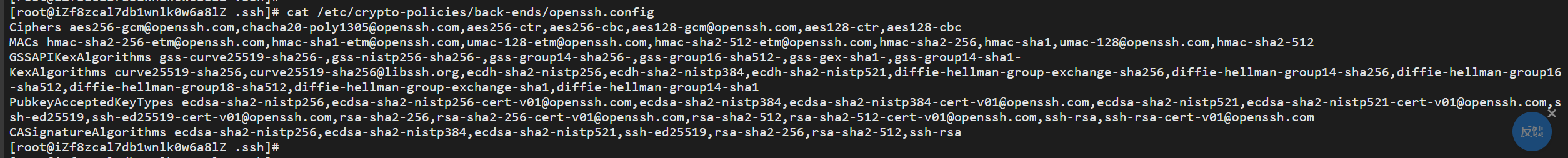
总结:禁用相关算法也是可以避免漏洞的一个途径。
附录:关于Windows平台的处理方法
1. 打开windows的Internet属性,找到高级–安全:取沟TLS1.0和1.1,只保留1.2;1.3也不勾选。
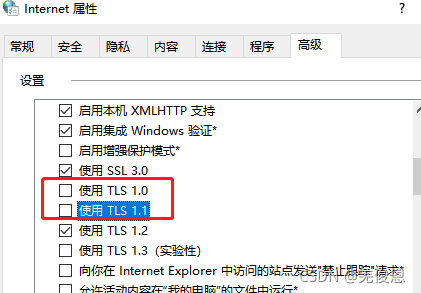
2. 打开组策略gpedit.msc,禁用弱密码算法即可。
3. 删除windows默认CA证书
参考文档
https://www.openssl.org/source/
https://openssl.org/news/secadv/20160922.txt






