Falco以及Falcosidekick输出类型汇总
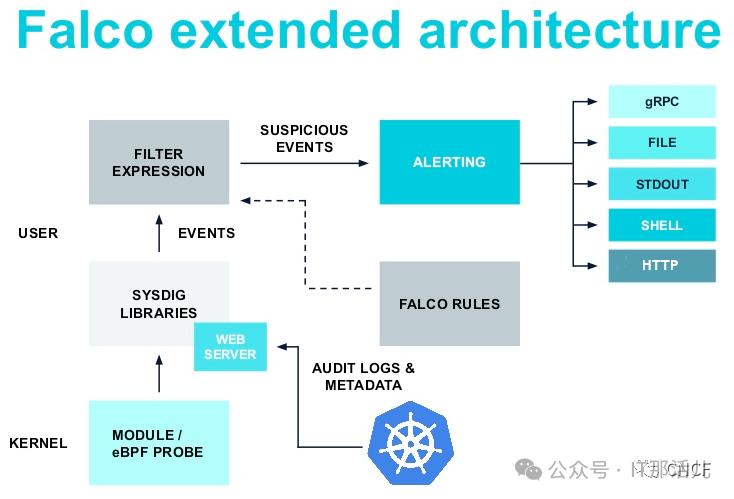
Chat
Slack Rocketchat Mattermost Teams Discord Google Chat Metrics Observability
Datadog Influxdb StatsD (for monitoring of falcosidekick) DogStatsD (for monitoring of falcosidekick) Prometheus (for both events and monitoring of falcosidekick) Wavefront Alerting
AlertManager Opsgenie PagerDuty Logs
Elasticsearch Loki AWS CloudWatchLogs Grafana (annotations) Syslog Object Storage
AWS S3 GCP Storage Yandex S3 Storage FaaS Serverless
AWS Lambda Kubeless OpenFaaS GCP Cloud Run GCP Cloud Functions Fission Message queue Streaming
NATS STAN (NATS Streaming) AWS SQS AWS SNS GCP PubSub Apache Kafka Kafka Rest Proxy RabbitMQ Azure Event Hubs Email
SMTP Web
Webhook WebUI (a Web UI for displaying latest events in real time)
部署Falco
$ helm repo add falcosecurity https://falcosecurity.github.io/charts
$ helm repo update
Hang tight while we grab the latest from your chart repositories...
...Successfully got an update from the "falcosecurity" chart repository
...Successfully got an update from the "stable" chart repository
Update Complete. ⎈Happy Helming!⎈复制
$ helm install falco falcosecurity/falco --set falco.jsonOutput=true --
set falco.httpOutput.enabled=true --set falco.httpOutput.url=http://falcosidekick:2801 -f howto/falcoCustomRule.yaml -n falco #这里的falcoCustomRule.yaml为自定义规则文件
NAME: falco
LAST DEPLOYED: Mon Nov 9 22:09:28 2020
NAMESPACE: default
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
Falco agents are spinning up on each node in your cluster. After a few
seconds, they are going to start monitoring your containers looking for
security issues.
No further action should be required.复制
$ helm ls
$ kubectl get pods复制
部署Falcosidekick
$helm install falcosidekick falcosecurity/falcosidekick --set config.slack.webhookurl=https://hooks.slack.com/services/xxxxxxxx --set webui.enabled=true -n falco
#输出
NAME: falcosidekick
LAST DEPLOYED: Thu Jan 14 23:55:12 2021
NAMESPACE: falco
STATUS: deployed
REVISION: 1
NOTES:
1. Get the application URL by running these commands:
export POD_NAME=$(kubectl get pods --namespace falco -l "app.kubernetes.io/name=falcosidekick,app.kubernetes.io/instance=falcosidekick" -o jsonpath="{.items[0].metadata.name}")
kubectl port-forward $POD_NAME 2801:2801
echo "Visit http://127.0.0.1:2801 to use your application"复制
注:关于hooks连接需要自主创建https://slack.com/intl/zh-cn/。
3.2 查看pod
$ kubectl get pod -n falco
NAME READY STATUS RESTARTS AGE
falco-9hftg 1/1 Running 0 89m
falco-gr5q7 1/1 Running 1 90m
falco-lpczj 1/1 Running 0 90m
falcosidekick-586bdb8c6b-j2wdf 1/1 Running 0 5h39m
falcosidekick-586bdb8c6b-zncvq 1/1 Running 0 5h39m
falcosidekick-ui-68f9444cbc-8x9b6 1/1 Running 0 40m复制
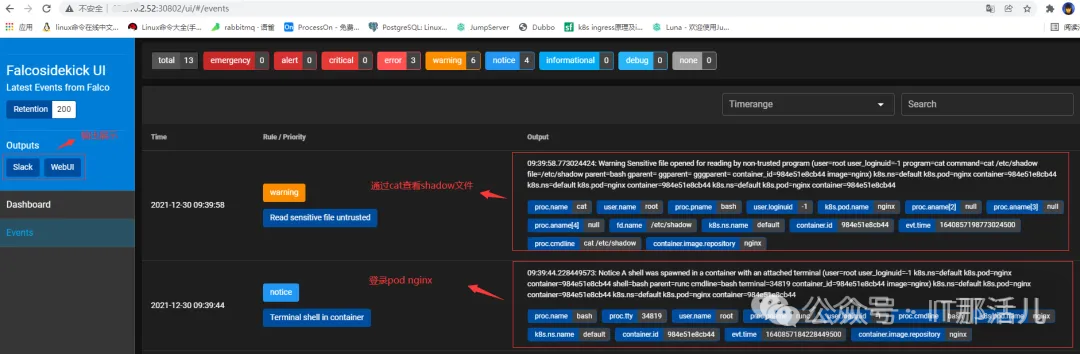
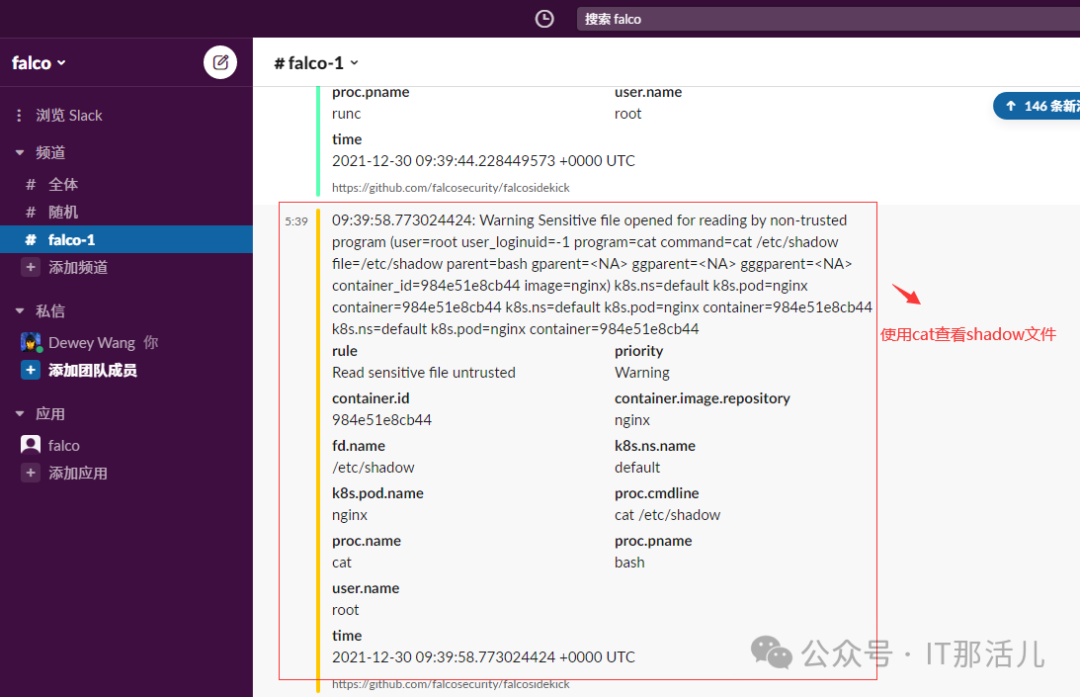
$kubectl logs deployment/falcosidekick -n falco
Found 2 pods, using pod/falcosidekick-586bdb8c6b-j2wdf
2021/12/30 03:42:06 [INFO] : Enabled Outputs : [Slack WebUI]
2021/12/30 03:42:06 [INFO] : Falco Sidekick is up and listening on :2801
2021/12/30 03:48:12 [INFO] : WebUI - Post OK (200)
2021/12/30 03:48:15 [INFO] : Slack - Post OK (200)复制
#查看svc
$kubectl get svc -n falco
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
falcosidekick ClusterIP XXX.106.191.244 <none> 2801/TCP 5h46m
falcosidekick-ui ClusterIP XXX.99.191.73 <none> 2802/TCP 5h46m
#修改svc类型
$kubectl edit svc -n falco falcosidekick-ui
.......
spec:
clusterIP: XXX.99.191.73
externalTrafficPolicy: Cluster
ports:
- name: http
nodePort: 30802 #添加NodePort端口,端口范围30000-32767
port: 2802
protocol: TCP
targetPort: http
selector:
app.kubernetes.io/instance: falcosidekick-ui
app.kubernetes.io/name: falcosidekick-ui
sessionAffinity: None
type: NodePort #改为NodePort类型
.......
#查看svc
$ kubectl get svc -n falco
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
falcosidekick NodePort XXX.106.191.244 <none> 2801:30801/TCP 5h46m
falcosidekick-ui NodePort XXX.99.191.73 <none> 2802:30802/TCP 5h46m复制
自定义规则
4.1 规则简介
元素 | 描述 |
|---|---|
Rules | 生成警报的触发条件。带有描述信息的规则和警报被一起发送 |
Macros | 在规则甚至其他宏中可重用的规则条件片段。宏提供了一种方法来命名常见模式和排除规则中的冗余。 |
Lists | 可以包含在规则、宏或其他列表中的项目集合。与规则和宏不同,列表不能被解析为过滤表达式 |
4.2 Rules规则
Key | Required | Description | Default |
|---|---|---|---|
rule | yes | 简短唯一的规则名称 | |
condition | yes | 检测事件与规则是否匹配的过滤表达式 | |
desc | yes | 规则检测内容的详细描述 | |
output | yes | 事件匹配时输出的消息,遵循 Sysdig 输出格式语法 | |
priority | yes | 事件严重性的表示(不区分大小写)。应该是以下之一:emergency、alert、critical、error、warning、notice、informational、debug。 | |
exceptions | no | 导致规则不生成警报的一组异常 | |
enabled | no | 如果设置为 false,则规则既不加载也不匹配任何事件。 | true |
tags | no | 应用于规则的标签列表 | |
warn_evttypes | no | 如果设置为 false,Falco 会禁止和事件无关的规则相关的警告 | true |
skip-if-unknown-filter | no | 如果设置为 true,如果规则条件包含过滤检查项,例如fd.some_new_field,而这个版本的Falco不识别此项,Falco默默的接受了规则但不执行;如果设置为 false,Falco 会遇到未知过滤检查项时报告错误。 | false |
4.2.1 Conditions条件
container.id != host and proc.name = bash复制
第一个子句检查事件是否发生在容器中(如果事件发生在常规主机上,Sysdig 事件的container字段等于“host”)。 第二个子句检查进程名称是否为 bash。
- rule: shell_in_container #规则名称
desc: notice shell activity within a container #规则注释
condition: container.id != host and proc.name = bash #条件过滤表达式(非常规主机下使用bash)
output: shell in a container (user=%user.name container_id=%container.id container_name=%container.name shell=%proc.name parent=%proc.pname cmdline=%proc.cmdline)
#匹配时输出信息
priority: WARNING #事件等级复制
4.2.2 Macros宏
- macro: in_container #宏名称
condition: container.id != host and proc.name = bash #条件过滤表达式复制
- rule: shell_in_container #规则名称
desc: notice shell activity within a container #规则注释
condition: (in_container) #条件过滤表达式(非常规主机下使用bash)
output: shell in a container (user=%user.name container_id=%container.id container_name=%container.name shell=%proc.name parent=%proc.pname cmdline=%proc.cmdline)
#匹配时输出信息
priority: WARNING #事件等级复制
4.2.3 Lists列表
- list: shell_binaries #列表名
items: [bash, csh, ksh, sh, tcsh, zsh, dash] #包含值
- list: userexec_binaries
items: [sudo, su]
- list: known_binaries
items: [shell_binaries, userexec_binaries] #包含其他列表
- macro: safe_procs condition: proc.name in (known_binaries) #条件(进程名为列表包含值)复制
4.3 附加到列表、规则和宏
附加Lists列表时,item被添加到List列表的末尾。 附加规则/宏时,附加文本将附加到条件:规则/宏的字段。
$ helm install falco falcosecurity/falco -f falcoCustomRule.yaml -n falco复制
falcoCustomRule.yaml复制
customRules:
falco_custom_network_rule.yaml: |-
- list: website_ips
items: ['"197.255.20.45"']
- rule: Connection to test or releaes
desc: Detect attempts to connect to yjp website
condition: outbound and fd.sip in (website_ips)
output: Outbound connection to yjp website http://www.release.yijiupidev.com or http://www.test.yijiupidev.com/(command=%proc.cmdline connection=%fd.name container_id=%container.id container_name=%container.name %container.info image=%container.image)
priority: WARNING
tags: [network]复制
可通过以正确的顺序使用多个 -r 参数来进行配置(本地安装); 通过 falco 配置文件 (falco.yaml) 中的rules_file; 使用官方 Helm Chart的 falco.rulesFile 值。
示例(本地安装):
falco -r /etc/falco/falco_rules.yaml -r /etc/falco/falco_rules.local.yaml复制
4.3.1 附加到列表
/etc/falco/falco_rules.yaml复制
- list: my_programs
items: [ls, cat, pwd]
- rule: my_programs_opened_file
desc: track whenever a set of programs opens a file
condition: proc.name in (my_programs) and evt.type=open
output: a tracked program opened a file (user=%user.name command=%proc.cmdline file=%fd.name) priority: INFO复制
/etc/falco/falco_rules.local.yaml复制
- list: my_programs #附加至my_programs列表名
append: true
items: [cp]复制
4.3.2 附加到宏
/etc/falco/falco_rules.yaml复制
- macro: access_file
condition: evt.type=open
- rule: program_accesses_file
desc: track whenever a set of programs opens a file
condition: proc.name in (cat, ls) and (access_file)
output: a tracked program opened a file (user=%user.name command=%proc.cmdline file=%fd.name) priority: INFO复制
/etc/falco/falco_rules.local.yaml复制
- macro: access_file #宏名称
append: true
condition: or evt.type=openat #附加规则条件复制
4.3.3 附加到规则
/etc/falco/falco_rules.yaml复制
- rule: program_accesses_file
desc: track whenever a set of programs opens a file
condition: proc.name in (cat, ls) and evt.type=open
output: a tracked program opened a file (user=%user.name command=%proc.cmdline file=%fd.name)
priority: INFO复制
/etc/falco/falco_rules.local.yaml复制
- rule: program_accesses_file #规则名称
append: true
condition: and not user.name=root #附加条件(user.name为root不触发)复制
4.3.4 规则/宏附加和逻辑运算符的问题
- rule: my_rule
desc: ...
condition: evt.type=open and proc.name=apache
output: ...
- rule: my_rule
append: true
condition: or proc.name=nginx复制
解释1:apache/nginx 打开文件或者 evt.type=open操作? 解释2:apache打开文件或者允许nginx做任何事情?
4.4 禁用默认规则
4.4.1 通过现有的宏
- macro: consider_all_outbound_conns
condition: (always_true)复制
4.4.2 通过 Falco 参数
-D <substring> Disable any rules with names having the substring <substring>. Can be specified multiple times.
-T <tag> Disable any rules with a tag=<tag>. Can be specified multiple times.
Can not be specified with -t.
-t <tag> Only run those rules with a tag=<tag>. Can be specified multiple times.
Can not be specified with -T/-D.复制
4.4.3 通过自定义规则
- rule: User mgmt binaries
append: true
enabled: false复制
- rule: User mgmt binaries
condition: and (never_true)
append: true复制
4.5 规则优先级
EMERGENCY ALERT CRITICAL ERROR WARNING NOTICE INFORMATIONAL DEBUG
如果规则与写入状态(即文件系统等)有关,则其优先级为 ERROR。 如果规则与未经授权的读取状态(即读取敏感文件等)有关,则其优先级为 WARNING。 如果规则与意外行为(在容器中产生意外的 shell、打开意外的网络连接等)有关,则其优先级为 NOTICE。 如果规则与违反最佳实践的行为有关(意外的特权容器、具有敏感挂载的容器、以 root 身份运行交互式命令),则其优先级为 INFO。 一个例外是规则“Run shell untrusted”,它有FP-prone,优先级为 DEBUG。
4.6 规则标签
- rule: File Open by Privileged Container
desc: Any open by a privileged container. Exceptions are made for known trusted images.
condition: (open_read or open_write) and container and container.privileged=true and not trusted_containers
output: File opened for read/write by privileged container (user=%user.name command=%proc.cmdline %container.info file=%fd.name)
priority: WARNING
tags: [container, cis]复制
您可以使用 -T 参数禁用具有给定标签的规则。-T 可以指定多次。 例如要跳过所有带有“filesystem”和“cis”标签的规则,你可以使用 falco -T filesystem -T cis .... 。-T 不能与 -t 一起指定。 您可以使用 -t 参数仅仅运行具有给定标记的规则。-t 可以指定多次。 例如,要仅运行带有“filesystem”和“cis”标签的规则,您可以使用 falco -t filesystem -t cis .... 。-t 不能与 -T 或 -D 一起指定(通过规则名称正则表达式禁用规则)。
4.6.1 当前 Falco 规则集的标签
4.7 规则条件最佳实践
Rule no_evttype: warning (no-evttype):
proc.name=foo
did not contain any evt.type restriction, meaning that it will run for all event types.
This has a significant performance penalty. Consider adding an evt.type restriction if possible.复制
Rule evttype_not_equals: warning (trailing-evttype):
evt.type!=execve
does not have all evt.type restrictions at the beginning of the condition,
or uses a negative match (i.e. "not"/"!=") for some evt.type restriction.
This has a performance penalty, as the rule can not be limited to specific event types.
Consider moving all evt.type restrictions to the beginning of the rule and/or
replacing negative matches with positive matches if possible.复制
4.8 转义特殊字符
- rule: Any Open Activity by Systemd
desc: Detects all open events by systemd.
condition: evt.type=open and proc.name="(systemd)" or proc.name=systemd
output: "File opened by systemd (user=%user.name command=%proc.cmdline file=%fd.name)"
priority: WARNING复制
- list: systemd_procs
items: [systemd, '"(systemd)"']
- rule: Any Open Activity by Systemd
desc: Detects all open events by systemd.
condition: evt.type=open and proc.name in (systemd_procs)
output: "File opened by systemd (user=%user.name command=%proc.cmdline file=%fd.name)"
priority: WARNING复制
4.9 忽略的系统调用
access alarm brk capget clock_getres clock_gettime
clock_nanosleep clock_settime close container cpu_hotplug
drop epoll_create epoll_create1 epoll_ctl epoll_pwait
epoll_wait eventfd eventfd2 exit_group fcntl fcntl64
fdatasync fgetxattr flistxattr fstat fstat64 fstatat64
fstatfs fstatfs64 fsync futex get_robust_list
get_thread_area getcpu getcwd getdents getdents64 getegid
geteuid getgid getgroups getitimer getpeername getpgid
getpgrp getpid getppid getpriority getresgid getresuid
getrlimit getrusage getsid getsockname getsockopt gettid
gettimeofday getuid getxattr infra io_cancel io_destroy
io_getevents io_setup io_submit ioprio_get ioprio_set k8s
lgetxattr listxattr llistxattr llseek lseek lstat lstat64
madvise mesos mincore mlock mlockall mmap mmap2 mprotect
mq_getsetattr mq_notify mq_timedreceive mq_timedsend mremap
msgget msgrcv msgsnd munlock munlockall munmap nanosleep
newfstatat newselect notification olduname page_fault pause
poll ppoll pread pread64 preadv procinfo pselect6 pwrite
pwrite64 pwritev read readv recv recvmmsg remap_file_pages
rt_sigaction rt_sigpending rt_sigprocmask rt_sigsuspend
rt_sigtimedwait sched_get_priority_max
sched_get_priority_min sched_getaffinity sched_getparam
sched_getscheduler sched_yield select semctl semget semop
send sendfile sendfile64 sendmmsg setitimer setresgid
setrlimit settimeofday sgetmask shutdown signaldeliver
signalfd signalfd4 sigpending sigprocmask sigreturn splice
stat stat64 statfs statfs64 switch sysdigevent tee time
timer_create timer_delete timer_getoverrun timer_gettime
timer_settime timerfd_create timerfd_gettime timerfd_settime times ugetrlimit umask uname ustat vmsplice wait4 waitid waitpid write writev复制
本文作者:汪训琪(上海新炬中北团队)
本文来源:“IT那活儿”公众号







