Kubernetes 审计(Auditing) 功能提供了与安全相关的、按时间顺序排列的记录集, 记录每个用户、使用 Kubernetes API 的应用以及控制面自身引发的活动。

1、修改kube-apiserver启动文件
# 修改apiserver启动参数
- --audit-policy-file=/etc/kubernetes/pki/audit-policy.yaml
- --audit-log-path=/var/log/kubernetes/audit.json
- --audit-log-maxage=3
- --audit-log-format=json
# 挂载审计目录
volumeMounts:
- mountPath: var/log/kubernetes
name: audit-log
volumes:
- hostPath:
path: var/log/kubernetes
type: DirectoryOrCreate
name: audit-log
Tip:修改/etc/kubernetes/manifests/kube-apiserver.yaml文件
2、审计记录规则
apiVersion: audit.k8s.io/v1beta1
kind: Policy
rules:
# 所有资源都记录请求的元数据(请求的用户、时间戳、资源、动词等等), 但是不记录请求或者响应的消息体。
- level: Metadata
Tip:上述内容写入到/etc/kubernetes/pki/audit-policy.yaml文件中
3、重启apiserver服务
sudo mv etc/kubernetes/manifests/kube-apiserver.yaml tmp
sudo mv tmp/kube-apiserver.yaml etc/kubernetes/manifests/kube-apiserver.yaml
复用往期 云原生日志流水线:Filebeat Helm化部署避坑指南 文章中的filebeat服务。
- type: log
enabled: true
fields:
log_topic: k8s-audit
paths:
- /var/log/kubernetes/audit.json
Tip:在 `daemonset.filebeatConfig.filebeat.inputs` 添加上述配置
$ helm -n obs-system upgrade filebeat -f filebeat-values.yaml filebeat
Release "filebeat" has been upgraded. Happy Helming!
NAME: filebeat
LAST DEPLOYED: Mon Mar 31 11:28:14 2025
NAMESPACE: obs-system
STATUS: deployed
REVISION: 2
TEST SUITE: None
NOTES:
1. Watch all containers come up.
$ kubectl get pods --namespace=obs-system -l app=filebeat -w
复用往期 打造百万级日志洪峰!Logstash容器化部署如何扛住压力? 文章中的logstask服务。
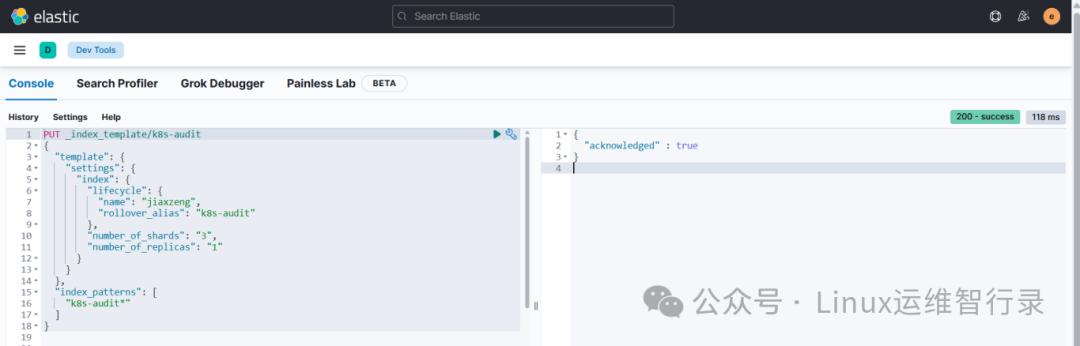
PUT _index_template/k8s-audit
{
"template": {
"settings": {
"index": {
"lifecycle": {
"name": "jiaxzeng",
"rollover_alias": "k8s-audit"
},
"number_of_shards": "3",
"number_of_replicas": "1"
}
}
},
"index_patterns": [
"k8s-audit*"
]
}
k8s-audit.conf: |
input {
kafka {
bootstrap_servers => "172.139.20.17:9095,172.139.20.81:9095,172.139.20.177:9095"
topics => ["k8s-audit"]
group_id => "k8s-audit"
security_protocol => "SASL_SSL"
sasl_mechanism => "SCRAM-SHA-512"
sasl_jaas_config => "org.apache.kafka.common.security.scram.ScramLoginModule required username='admin' password='admin-password';"
ssl_truststore_location => "/usr/share/logstash/certs/kafka/kafka.server.truststore.p12"
ssl_truststore_password => "truststore_password"
ssl_truststore_type => "PKCS12"
}
}
filter{
json{source=>"message"}
mutate{
remove_field=>["@timestamp","@metadata","log","fields","input","ecs","agent"]
}
}
output{
elasticsearch{
hosts=>["https://elasticsearch.obs-system.svc:9200"]
ilm_enabled=>true
ilm_rollover_alias=>"k8s-audit"
ilm_pattern=>"{now/d}-000001"
ilm_policy=>"jiaxzeng"
manage_template=>false
template_name=>"k8s-audit"
user=>"elastic"
password=>"admin@123"
ssl=>true
ssl_certificate_verification=>true
truststore=>"/usr/share/logstash/certs/es/http.p12"
truststore_password=>"http.p12"
}
}
Tip:在 `logstashPipeline` 添加上述配置
$ helm -n obs-system upgrade logstash -f logstash-values.yaml logstash
Release "logstash" has been upgraded. Happy Helming!
NAME: logstash
LAST DEPLOYED: Mon Mar 31 15:44:47 2025
NAMESPACE: obs-system
STATUS: deployed
REVISION: 14
TEST SUITE: None
NOTES:
1. Watch all cluster members come up.
$ kubectl get pods --namespace=obs-system -l app=logstash -w
`Stack Management` -> `Index patterns`
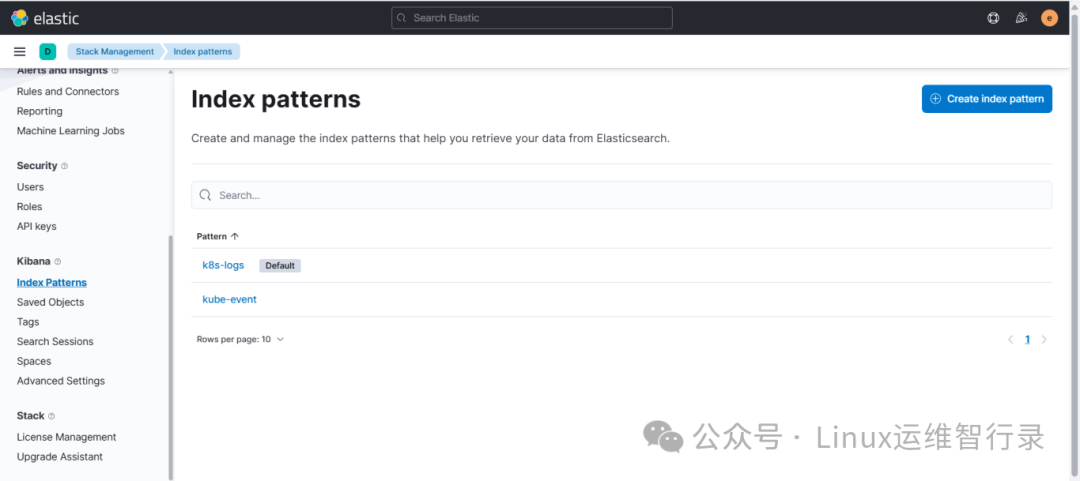
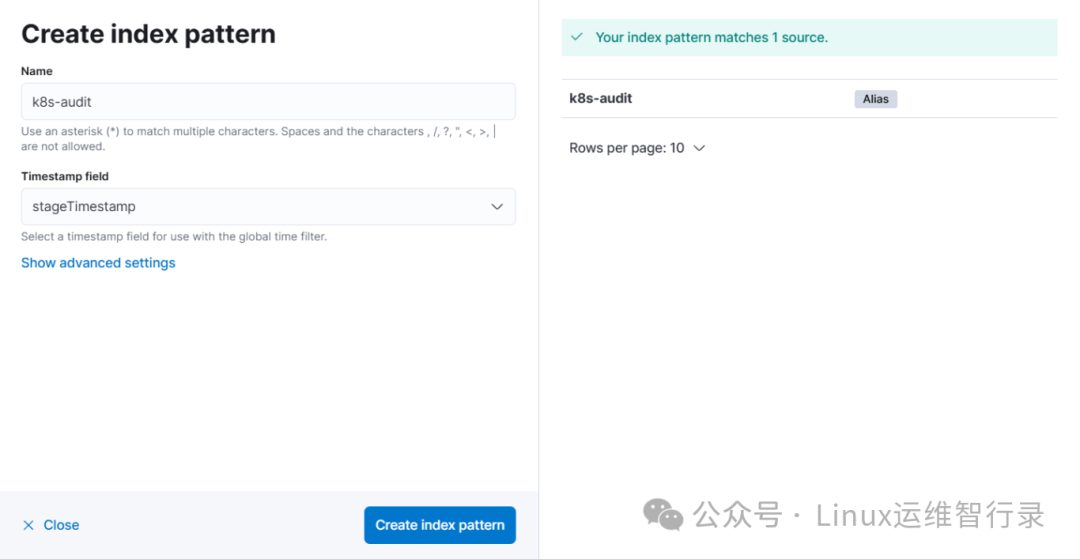
`Create index pattern`
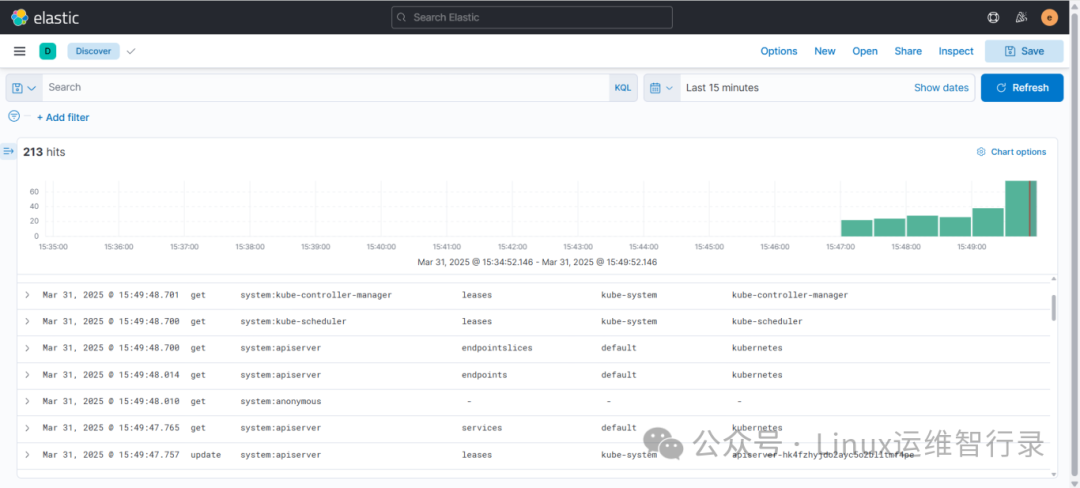
Tip:`Analytics -> Discover`
当最后一个高危操作告警规则通过自动化测试,安全团队终于可以从“救火模式”切换到“预警模式”——但这只是开始。
【推荐阅读】点击下方蓝色标题跳转至详细内容!
别忘了,关注我们的公众号,获取更多关于容器技术和云原生领域的深度洞察和技术实战,让我们携手在技术的海洋中乘风破浪!
文章转载自Linux运维智行录,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






