As I introduced before, we use the strategy from business to IT, top-down strategy to manage the architecture of the enterprise. Always take data as the core factor, through the effective management of data and Continue to mine the value of data,keep delivering digital thinking to every organization and individual, ensure the continuous and efficient operation of the business and help enterprises make better decisions. embracing the smart, data-driven future.
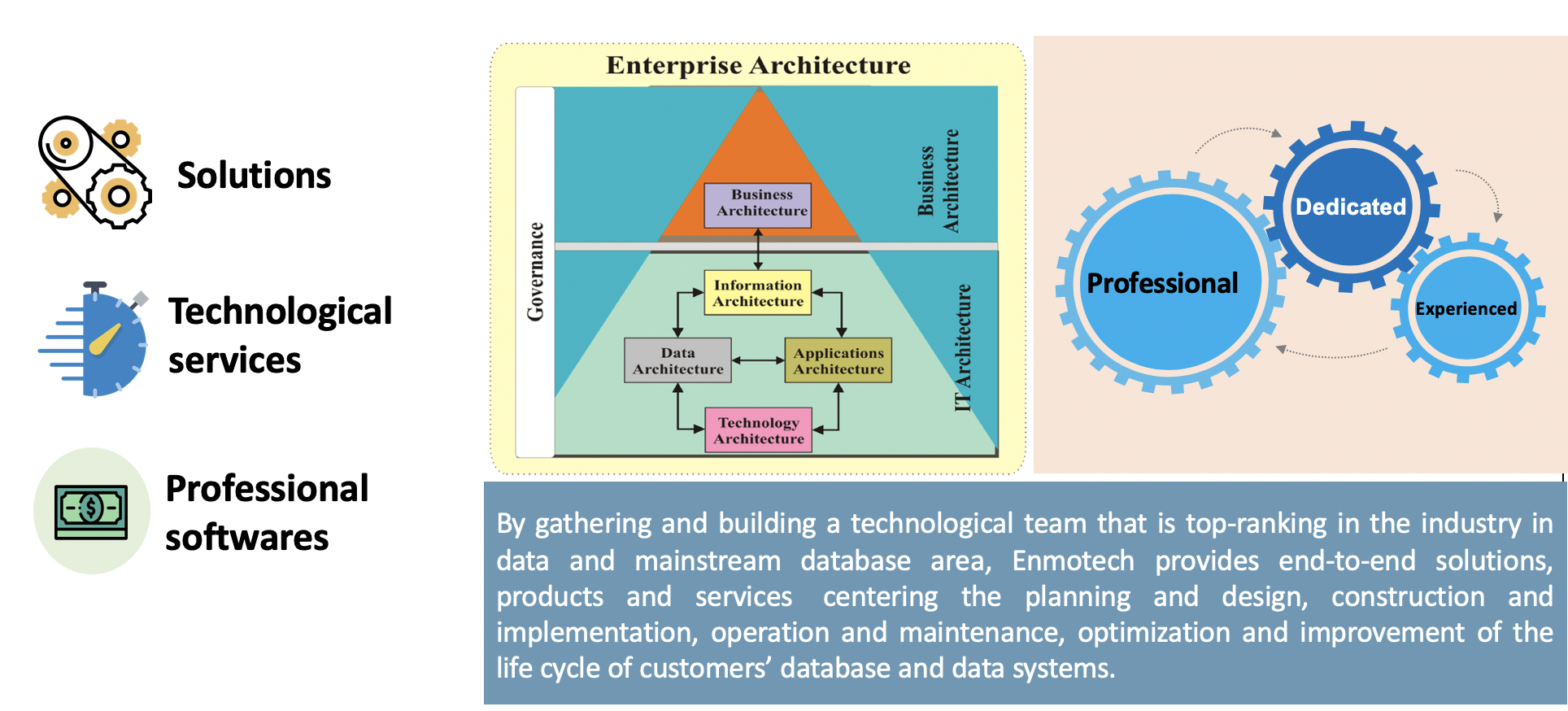
Over these years, we bringing together top experts in the field, which keeps us professional. We have served thousands of enterprise customers, so we have accumulated a lot of experience in the industry. We have formed a good service system that can respond to customer needs 7*24. All round the clock.
Through our professional team and years of industry experience, we maximize the value of data. Aimed to help companies achieve their four goals in data area:
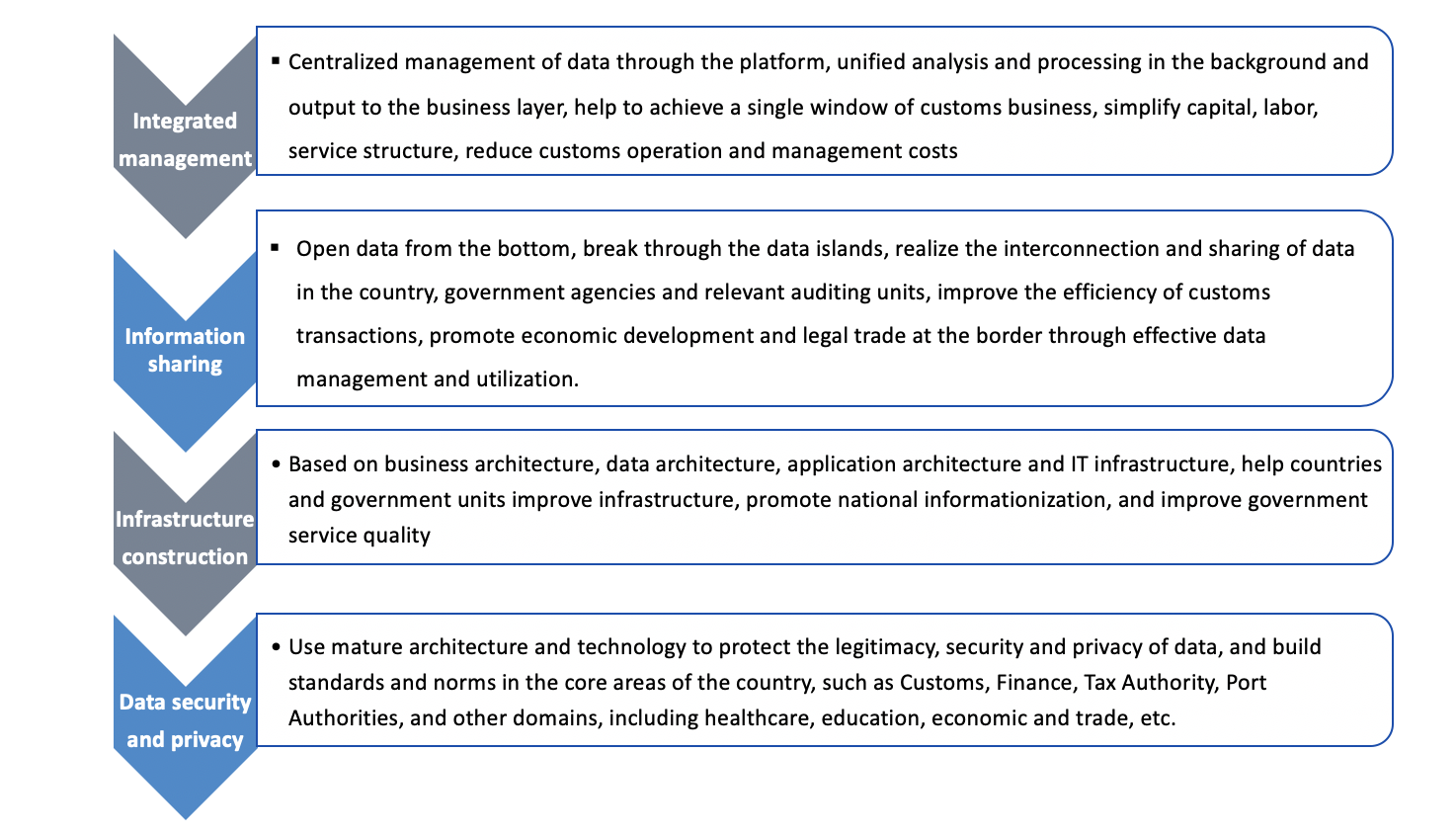
1. Data security and personal privacy protection
First of all, to ensure the security of the data, avoid data being stolen or illegally used, to ensure that personal privacy data will not leak.
2. Construction of data infrastructure
Establish specifications and standards for data storage, and build unified framework of data
3, to achieve information sharing
Meaning open up information islands, build interconnection between data solos to make data available and allowed being accessed between systems to avoid data errors and inconsistencies.
For example, for most online business, we have to register and create an account, there are some necessary information needed, such as username, phone number, email, job title, and etc.
But this kind of information isn’t always the same, we change the phone number, use different email, sometimes I give myself different names, after all it’s just a username, not my ID.
But let’s see what kind of problem would be brought in?
One day I may forget my password and can’t get it back, so to get the transaction done,I register another account, but use another phone number, but system doesn’t know that, it takes me as a new account, so both two of my account information would be keep, there is a lot of redundancy.
And for me, I have to remember all the account information for all sites, the truth for me is, I forget most of them. I bet this kind of thing happened to you, am I right?
So my biggest problem used to be where is my key?
but now it’s absolutely what’s my password?
Well you see it would be a better world if we can just share the account information, right?
4. to achieve centralized management and unified analysis modeling
Based on the data sharing, unified modeling and analysis can be achieved through new technologies, big data and artificial intelligence, to help business decisions.
The data protection and management run through the entire lifecycle of IT construction.
In the first phase, design and plan the IT system according to the needs of the business to ensure maximum support and response to the business.
The second phase, we help the IT personal of enterprise to deploy and implement the system, including the installation of the basic environment, hardware, network, operate system, database, and deployment of high-availability and backup architecture, like read only separation, Cluster etc.
The third phase is the operation and management. After the business went public, the system needs to be managed and maintained to ensure the continuity and efficient operation of the business.
Finally, through data management optimization, improve business efficiency and enhance user experience. and also if the performance goes down or the system crush, we help them complement disaster recovery, minimize the loss.
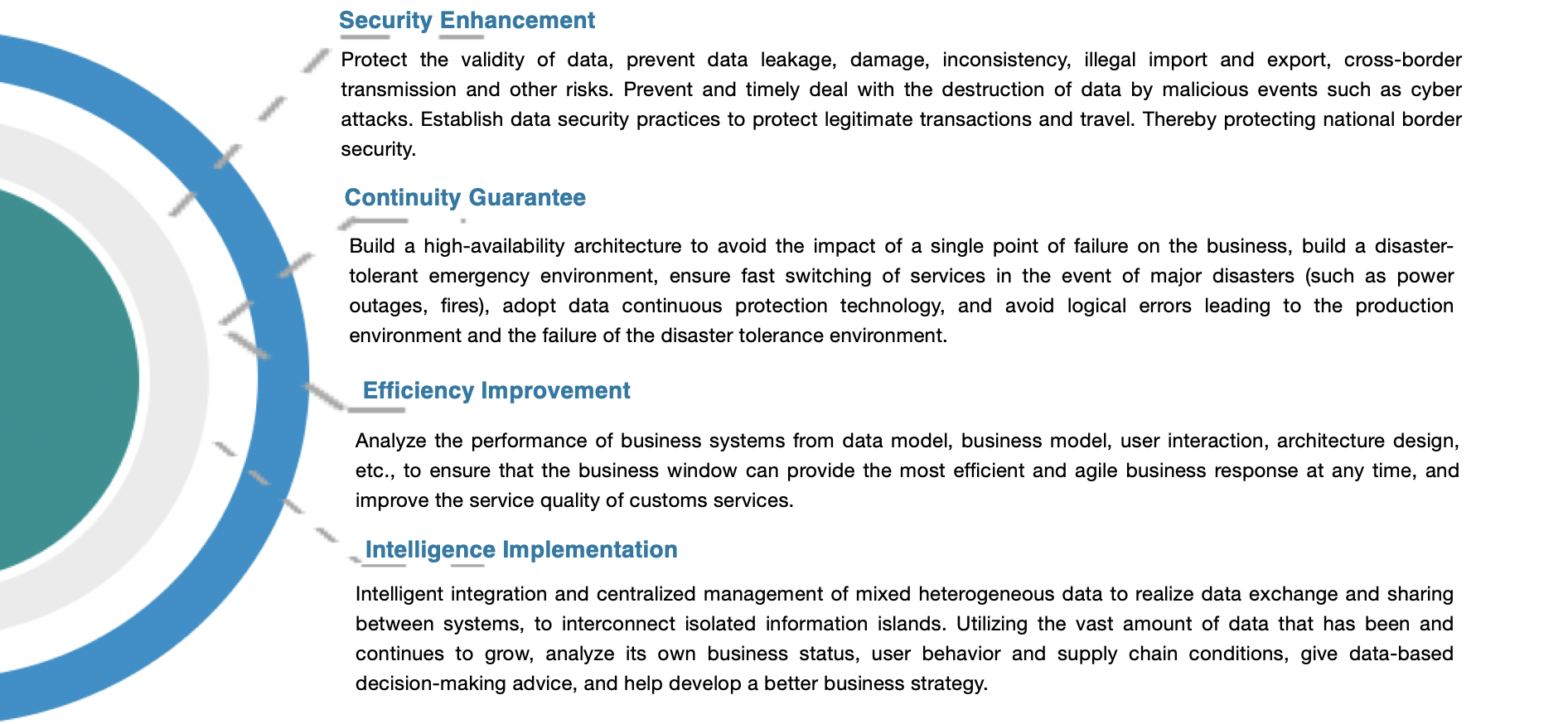
Specifically, for these four phases, the whole lifecycle of IT system, our data management solutions include:
- Security Enhancement
- Continuity Guarantee
- Efficiency Improvement
- Intelligence Implementation
Horizontally, the range of technologies filed we can deliver and support, including commercial databases like Oracle, DB2, SQL Server,Open source database, MySQL, postgreSQL, etc. And mainstream middleware.

Vertically, our business scope cover from infrastructure to business. both for the entire life cycle of IT construction and the entire life cycle of data from been generated to been operation.
In addition to an integrated solution, we also provide professional services focus on the database area, because database is the most essential part of the IT.
We provide professional consulting services at the beginning of IT system construction to help users do architectural design and technology selection
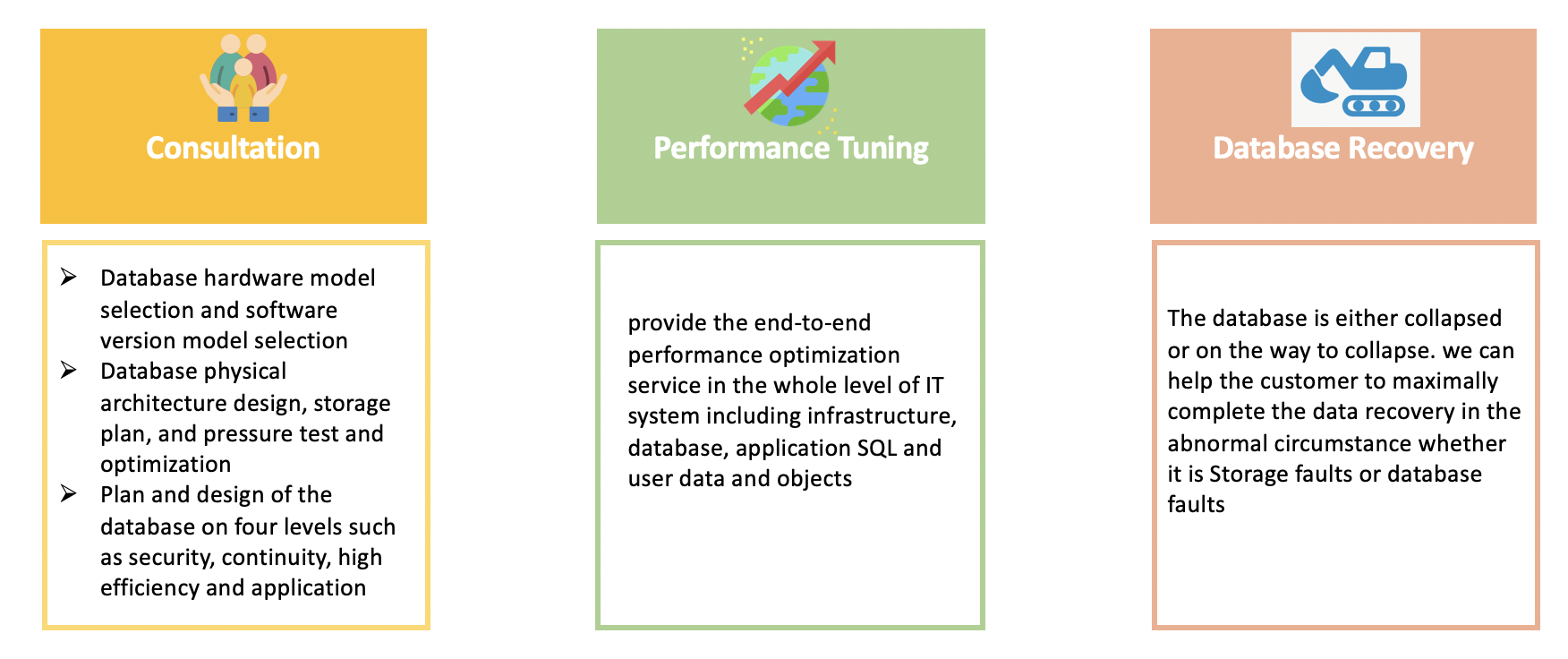
After the application is launched, we provide top-down performance tunning services to ensure the operational efficiency for best user experience.
If extreme situations result in data being corrupted or lost, we can also help with disaster recovery, minimize RPO and RTO, and reduce corporate losses.
We have done emergency data recovery and rescue for many companies. For example, last month’s CMBI bank from Philippine MySQL database failure caused business disruption, people can’t get any money out of their account and there was a lot of complaints. Our technicians responded promptly after receiving the demand, helping customers solve the problem and making a better data backup protection strategy.
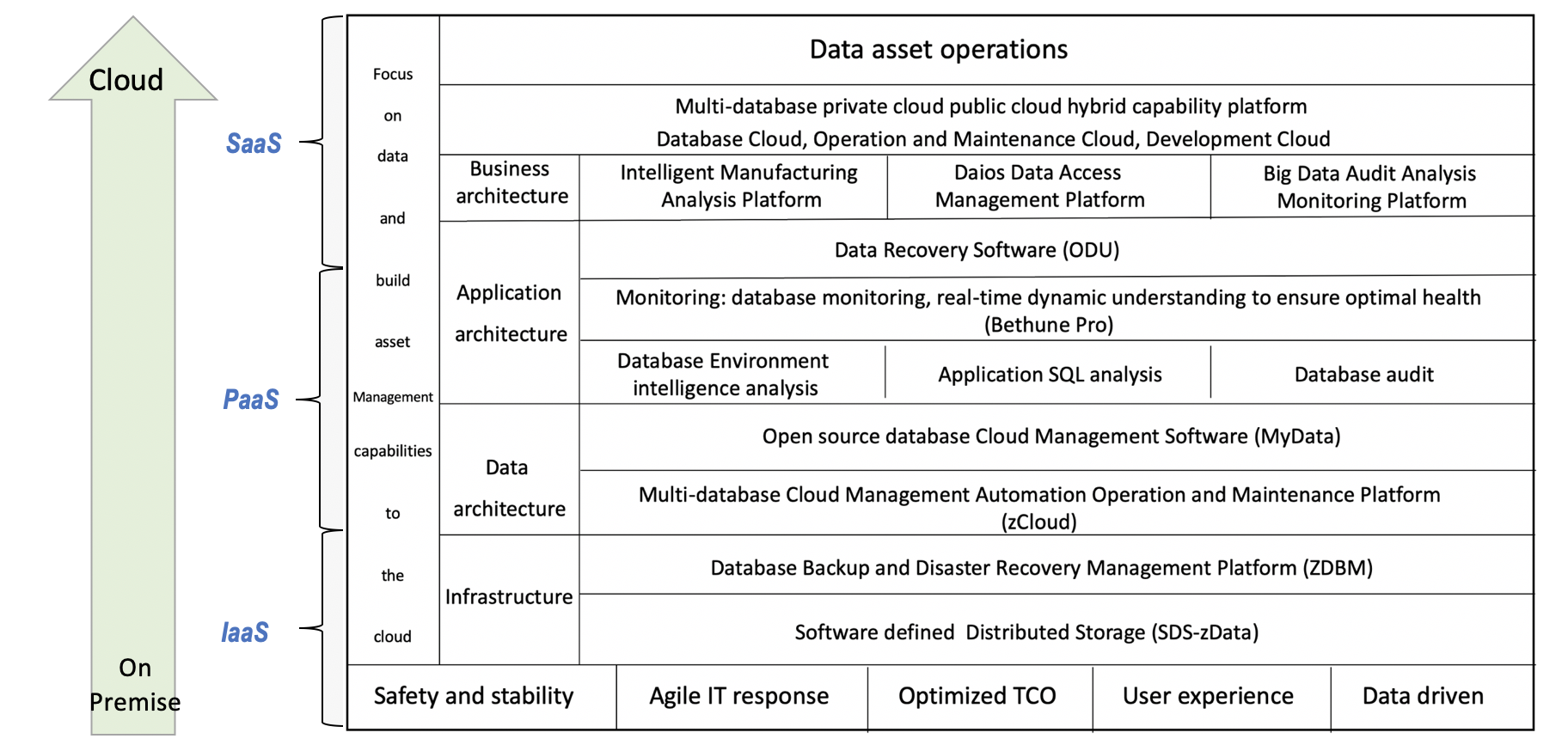
Here I illustrated our product family
Based on the five core requirements of IT system construction, that is security and stability, agile support, TCO optimization, user experience, data-driven business innovation
Our product portfolio spans IT infrastructure to business areas, helping customers build local and cloud service support capabilities.
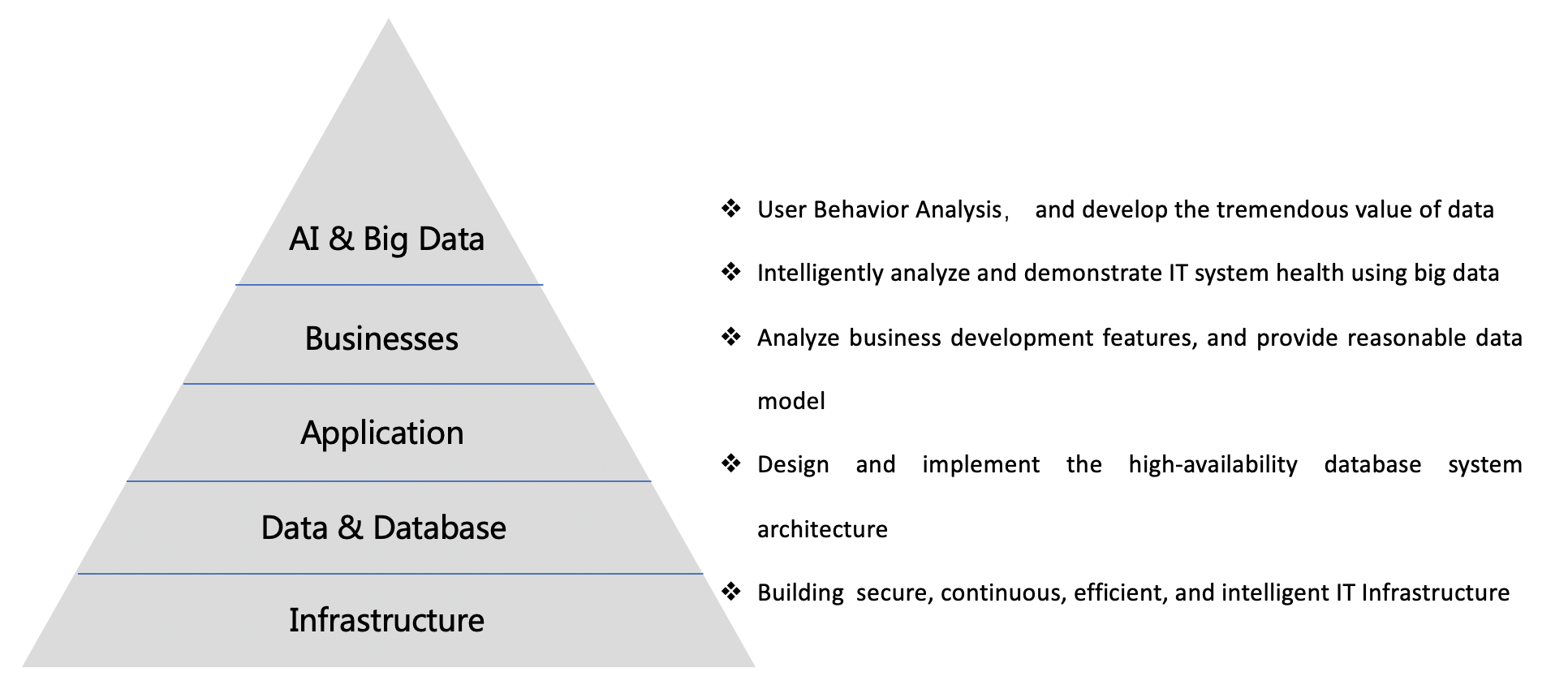
In the perspective of the functional modules, from bottom-up, our products can be put into four different layer:
- The layer of infrastructure, including zData:software-defined distributed storage, as the bearer environment of the business information like account information and transaction data.
ZDBM:Database backup and recovery management software to help ensure continuity in extreme situations and protect data from loss.
-
The layer of data architecture, also can be referred to as Platform, cloud management software including zCloud multi-database automated operation and maintenance platform and MyData open source database cloud management .
-
The layer of application is our series of operation and maintenance management software. Through security audit, database monitoring, SQL statement auditing, etc., to ensure system running with best performance.
-
The layer of business. is an analysis-based business using artificial intelligence and big data, including intelligent manufacturing modeling analysis, corporate internal audit, etc.
Based on these business modules, we are building a cloudy hybrid capability platform that includes both public and private clouds for truly integrated data asset operations.
To be continued






