




C刊-Research_on_Quantum_SSL_Based_on_National_Cryptography.pdf
免费下载
Research on Quantum SSL Based on National
Cryptography
Yuqian Lu
School of Cyber Science and
Engineering
Southeast University
Nanjing, China
220215474@seu.edu.cn
Liping Wei
Department of Cyberspace
Security
ZTE Corporation
Shenzhen, China
wei.liping@zte.com.cn
Wenfang Wu
School of Cyber Science and
Engineering
Southeast University
Nanjing, China
220224928@seu.edu.cn
Yuang Zhang
School of Cyber Science and
Engineering
Southeast University
Nanjing, China
220235225@seu.edu.cn
AbstractSecure Socket Layer (SSL) is an extensively
deployed secure connection protocol. However, with the advent of
quantum computing technology, the SSL protocol based on
traditional keys presents security concerns. In this paper, we
proffer a novel scheme that combines the SSL protocol with the
national cryptographic algorithm, along with the incorporation of
quantum keys to address the foreseen quantum security concerns.
Furthermore, we leverage post-quantum cryptography techniques
to augment and refine the current encryption suit. Experimental
evidence indicates that the SSL communication system outlined in
this study exhibits good performance regarding throughput and
latency, bolstering the security of data transmission.
Keywords—SSL, Quantum Cryptography, Post-Quantum
Cryptography, National Secret Algorithms
I. INTRODUCTION
With the advent of quantum computing technology,
traditional encryption algorithms will no longer be able to ensure
the security of network communications. The RSA algorithm,
which underpins the SSL protocol, derives its security from the
computational difficulty associated with factoring large prime
numbers. However, the advent of Shor's algorithm, which
efficiently solves prime factorization and discrete logarithm
problems, poses a direct threat to the security of traditional
public key cryptosystems[1]. Therefore, it is necessary to
explore new methods from the SSL protocol to fundamentally
solve the security problems caused by quantum computing
attacks. Quantum cryptography and post-quantum cryptography
are powerful weapons to solve this problem.
Quantum Key Distribution (QKD) possesses the capability
to withstand quantum computing assaults, a strength derived
from the inseparability of single quantum states and the inability
to clone[2]. Thus, QKD provides an unconditionally safe
security paradigm from a theoretical standpoint. During the
quantum key distribution, the QKD equipment will generate
quantum keys and their corresponding serial numbers through
quantum key agreement protocols (such as BB84/B92/TF-
QKD)[3]. After generation, a key pool stores these keys which
facilitates the uniform authentication and management of each
quantum key and their identifier counterparts[4]. The
application of quantum keys to encrypted communication
systems can notably improve the overarching system security
profile. Mohamed [5] etc presented a novel extension of the TLS
protocol based on quantum cryptography, improving the
security of the process of authentication and data encryption.
However, this scheme does not perform quantum key consensus
negotiation.
Post-quantum cryptography is a cryptographic algorithm
developed to address security threats in the quantum computer
era. These post-quantum cryptographic algorithms can outpace
the computation speed of extant public key cryptosystems while
maintaining an equivalent security level[6]. Chan[7] etc
presented a post-quantum SSL library using publicly available
parameters, adapting the library from Polar SSL rather than the
more popular Open SSL. Crocket[8] etc examined various
design considerations for integrating post-quantum and hybrid
key exchange and authentication into communications protocols
generally and in TLS and SSH specifically. Yevseie[9] etc
proposed an improved protocol based on post-quantum
algorithms, which used the Niederreiter crypto-code
constructions and the improved UMAC algorithm. Schwab[10]
etc presented an alternative to the TLS handshake that uses a
key-encapsulation mechanism instead of signatures for server
authentication. In our study, we will use a post-quantum
algorithm called CRYSTALS-Kyber. Its security depends on the
difficulty of solving the Module Learning with Errors (MLWE)
problem[11]. When the parameters are appropriately selected,
there is currently no known algorithm that can quickly solve this
problem, so this algorithm has high security against quantum
attacks. Kyber has defined a total of three parameter sets, called
Kyber512, Kyber768, and Kyber1024[12]. The application of
post-quantum cryptography to SSL protocol can more
effectively deal with possible attacks such as quantum
computing in the future.
This study integrates quantum keys and post-quantum
algorithms into the SSL protocol framework, supplemented by
national cryptographic algorithms to expand the original key
source and solve the above security problem. When the user
selects a quantum cipher suite, the system can provide resistance
to quantum attacks based on its physical properties; when the
user selects a post-quantum cipher suite, the system can provide
resistance to quantum attacks based on its mathematical
properties. Simultaneously, the proposed system can
intelligently transition between quantum key mode and post-
260
2024 The 9th International Conference on Computer and Communication Systems
979-8-3503-5021-0/24/$31.00 ©2024 IEEE
2024 9th International Conference on Computer and Communication Systems (ICCCS) | 979-8-3503-5021-0/24/$31.00 ©2024 IEEE | DOI: 10.1109/ICCCS61882.2024.10603232
Authorized licensed use limited to: ZTE CORPORATION. Downloaded on November 26,2024 at 05:49:02 UTC from IEEE Xplore. Restrictions apply.
quantum encryption mode based on real-time conditions,
thereby providing an adaptive mechanism designed to resist
quantum attacks effectively. This study can significantly
enhance the security and reliability of data transmission, thereby
achieving a higher standard of data protection.
II. BACKGROUND
A. SSL Protocol
Secure Sockets Layer (SSL) is a secure transmission
protocol located between the application layer and the transport
layer in the TCP/IP protocol[12]. It operates by establishing an
encrypted link between a client and a server, ensuring that the
data transmitted between them remains confidential and
integral[13]. The SSL protocol defines a set of encryption
algorithms and key exchange methods as cipher suites, which
are negotiated and used to generate session keys during the SSL
handshake process[14]. Choosing the appropriate cipher suite is
crucial for ensuring the security of communication.
B. National Secret Algorithms
National secret algorithms are mainly divided into three
categories: symmetric cryptographic algorithms, asymmetric
cryptographic algorithms, and hash algorithms[15]. Among
them, SM2 is an asymmetric encryption algorithm, mainly used
for certificate verification and key negotiation[16]. SM3 is
suitable for scenarios such as digital signature and message
verification scenarios. It is an algorithm improved based on
SHA-256 and has high security[17].SM4, as the block cipher
standard for commercial ciphers in my country, is mainly used
in data encryption scenarios[18]. In the national secret SSL
protocol of this article, the SM4 algorithm can be used for data
encryption.
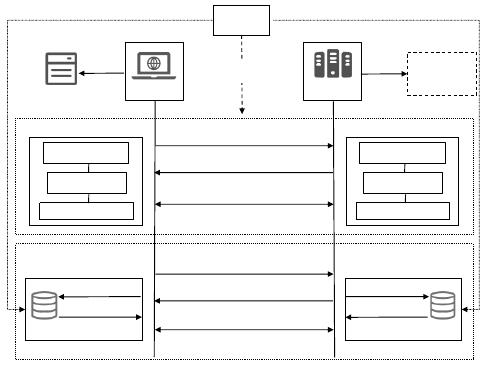
III. SYSTEM ARCHITECTURE
The system architecture designed in this paper is shown in
Fig.1.
Fig. 1. System architecture.
The quantum key storage device is abstracted as a Quantum
Key Pool (QKP). When the remaining quantum key quantity in
the pool meets the requirements, this approach uses the quantum
key negotiated by the Quantum Key Distribution (QKD) system
as the session key for the SSL protocol and introduces national
cryptographic algorithms to enhance security. When the
remaining quantum key quantity in the pool does not meet the
requirements, it automatically switches to a post-quantum
cryptographic mode. The primary objective of the system
architecture design is to seamlessly blend QKD with existing
security protocols and switch to the post-quantum cryptographic
algorithm when necessary.
A. SSL Handshake Process Based on National Cryptography
under the Quantum Mode
In the SSL handshake process operating in quantum mode,
the client first selects a quantum key from the key pool for use
in the subsequent sessions. This selected quantum key is then
combined with its associated key identifier and hashed by the
SM3 algorithm. The hash value obtained is then included in the
client's random number A, calculated as shown in (1):
( )
3 A SM Key _ Id QKD _ Key=+
()
Where
eyK _ Id
,
QKD_ Key
respectively represented the
quantum key identifier and quantum key. The client sends the
server a Client Hello request, principally informing the server of
its supported protocol version, random number A, encryption
method, and other necessary information.
Upon receiving the client's request, the server traverses
the .txt file where quantum keys are stored, seeking a data set
that satisfies the condition "SM3(Quantum Key Identifier,
Quantum Key) = Random Number A". If such a data set is found,
the identifier of the quantum key mode is set to 1, indicating that
the quantum key in this data set becomes the session master key
for subsequent communications between the two parties.
Conversely, if no matching data is found, the identifier is set to
0, implying that the communication will proceed using session
keys negotiated in the traditional mode, without utilizing
quantum keys.
Ultimately, the value of this identifier replaces the last digit
of the random number B destined for the client and is transmitted
via a Server Hello request. Additionally, the server selects a
national cryptographic suite from the cipher suites provided by
the client for subsequent communication and sends the
corresponding national cryptographic certificate to the client for
identity verification. Upon receiving the server's response, the
client validates the server's certificate and processes the received
server random number B. Based on the last digit of the random
number B, the client determines whether the server supports the
quantum key as the master key for communication.
Subsequently, the client encrypts and sends the random number
C using the server's SM3 public key. Upon receiving the
encrypted random number C, the server decrypts it with its own
SM3 private key.
The server and client generate the session master key
through random numbers A, B, and C. When the remaining
quantum key quantity in the key pool meets the requirements,
the quantum key mode is adopted. Both communicating parties
replace the previously generated master key with the negotiated
quantum key. At this point, the identity authentication and key
negotiation processes between the parties are completed, and
261
Authorized licensed use limited to: ZTE CORPORATION. Downloaded on November 26,2024 at 05:49:02 UTC from IEEE Xplore. Restrictions apply.
of 6
免费下载
【版权声明】本文为墨天轮用户原创内容,转载时必须标注文档的来源(墨天轮),文档链接,文档作者等基本信息,否则作者和墨天轮有权追究责任。如果您发现墨天轮中有涉嫌抄袭或者侵权的内容,欢迎发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。
下载排行榜


文档被以下合辑收录
评论