1. 什么是威胁建模
是一个可以识别和列举潜在威胁、漏洞或缺乏保护措施的过程。然后可以优先考虑缓解措施
通过安全性的视角查看应用程序及其环境。
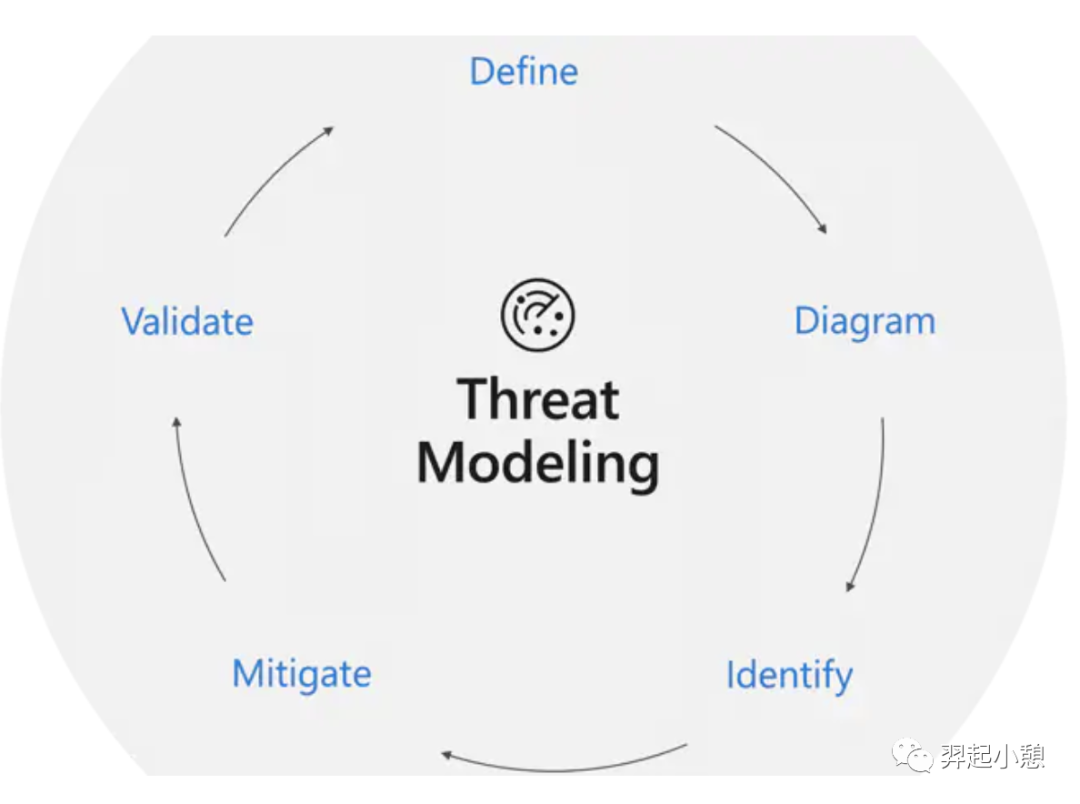
2 . 威胁建模的目的
是为防御者提供分析,分析需要包含哪些控制或防御措施,考虑到系统的性质、可能的攻击者的概况、最可能的攻击向量以及攻击者最需要的资产。生活中威胁建模例子:识别威胁 ->防护措施
We identified the threat of infection from other people, or from surfaces we touch, or the threat of infecting other people. Then we thought about ways to thwart those threats by keeping social distance, washing our hands more, wearing masks. Every interaction we have is considered and measured for threats from the virus. That’s an example of threat modeling.
3. 威胁建模的组成
A threat model typically includes:
Description of the subject to be modeled
Assumptions that can be checked or challenged in the future as the threat landscape changes
Potential threats to the system
Actions that can be taken to mitigate each threat
A way of validating the model and threats, and verification of success of actions taken
4. STRIDE 方法论
| 元素 | 含义 | 预防办法 |
| 欺骗攻击 | 是指一个人或程序伪造数据以获得非法优势,成功识别为另一个人或程序。 | 下载可信来源的app 使用行业标准认证协议 |
| 篡改 | 指多种形式的破坏,但该术语通常是指故意修改产品,使其对消费者有害 | 扫描代码漏洞 使用标准的加密融洽平台 |
| 否认 | 在数字安全中,不可否认性是指提供数据完整性和来源证明的服务,或以高可信度确定为真实的身份验证。 | 使用可靠且功能齐全的日志记录服务 |
| 信息披露 | 对数据技术或隐私的有害传播。有法律和政治问题需要考虑。信息披露是对数据隐私或数据保护的侵犯。数据隐私的挑战是在使用数据的同时保护个人的隐私偏好及其个人身份信息。 | 妥善管理安全证书并帮助加密数据传输 |
| 拒绝服务攻击 | (有时称为 DoS 攻击)是一种网络攻击,攻击者试图通过暂时或无限期地中断连接到 Internet 的主机的服务,使其目标用户无法使用机器或网络资源。 | 使用可靠的公共云托管工具 速率限制 |
| 权限提升 | 是利用操作系统或软件应用程序中的错误、设计缺陷或配置疏忽来获得对通常不受应用程序或用户保护的资源的更高访问权限的行为。 | 有很多层需要考虑特权:数据库管理、端点管理、容器管理,并且有许多管理这些层的方法:
|
5. 威胁建模:四个问题框架
A possible threat exists when the combined likelihood of the threat occurring and impact it would have on the organization create a significant risk. The following four question framework can help to organize threat modeling:
What are we working on?
What can go wrong?
What are we going to do about it?
Did we do a good job?
6. 评估范围
What are we working on? This might be as small as a sprint, or as large as a whole system.
Identify what can go wrong - This can be as simple as a brainstorm, or as structured as using STRIDE, Kill Chains, or Attack Trees.
Identify countermeasures or manage risk - Decide what you’re going to do about each threat. That might be to implement a mitigation, or to apply the accept/transfer/eliminate approaches of risk management.
Assess your work - Did you do a good enough job for the system at hand?
参考:
https://owasp.org/www-community/Threat_Modeling
https://www.microsoft.com/en-us/securityengineering/sdl/threatmodeling
https://www.threatmodelingmanifesto.org/






